Want to join in? Respond to our weekly writing prompts, open to everyone.
from  Kroeber
Kroeber
#002305 – 20 de Setembro de 2025
Kat Abughazaleh no meu ecrã, à procura do melhor remédio.
Lent 2026 Day 19 & 20 - Daylight
from Dallineation
I forgot to write a post yesterday. My first church meeting started at 9am and between all the church meetings, phone calls with family, and meals somewhere in there, I wasn't free until about 8pm. Add Daylight Saving Time starting and having to take allergy medicine that makes me sleepy on top of all of that and I was pretty wiped out at the end of the day.
But rather than feeling weighed down by it all as I have most Sundays for the past several months, I felt light. I felt at peace.
Rather than being frustrated and overwhelmed at the thought of everything I should be doing but am not doing or doing well, I felt like my best efforts, however meager, are still making a difference and are acceptable to God.
Rather than feeling ashamed and hypocritical that I still have questions and doubts, I knew that I was not the only one, that God does not love us any less.
I chatted with my bishop for a few minutes in between meetings.
“You seem different. You seem better,” he said.
“I am,” I replied. “I've had some spiritual experiences this week that have reaffirmed some things for me and helped me recalibrate my perspective. I still have questions, but I know I'm going to be ok.”
It's as if the sun is starting to rise on my spirit after a long, dark night. And while I know that there will be more dark nights in my life, I also know that I'm never alone.
#100DaysToOffload (No. 149) #faith #lent #Christianity
The Day the Builder Remembered the Rock
from Douglas Vandergraph
There is a quiet tragedy that unfolds every day in the lives of people who began with pure intentions. It does not usually happen loudly. It rarely announces itself with flashing warning signs or dramatic collapse. Instead, it creeps in slowly through long workdays, ambitious goals, spreadsheets, marketing strategies, deadlines, and the relentless pressure to make something succeed. A Christian entrepreneur may begin their journey kneeling in prayer, dedicating their dream to God, asking Him to bless the work of their hands, and promising that everything they build will be for His glory. But somewhere along the road between inspiration and expansion, something subtle can shift within the heart. The dream that once felt like a calling can slowly become a machine that demands constant feeding, and the One who inspired the vision can begin to fade quietly into the background. The business still carries Christian language, Christian branding, Christian mission statements, and perhaps even Bible verses on the office wall, but the daily decisions that determine the direction of the enterprise are no longer flowing from the same place of surrender that existed in the beginning.
This is not usually done with malicious intent. In fact, it often happens to the most sincere believers. People who love God deeply and who genuinely want to serve Him can slowly become consumed by the responsibilities of building something that requires endless attention. The demands of leadership have a way of filling every available space in a person's mind, and the urgency of business decisions can begin to drown out the quieter voice of spiritual guidance. Many Christian entrepreneurs wake up one day and realize they are exhausted, spiritually dry, and wondering why something that once felt alive now feels strangely hollow. The numbers might still be moving. The company may still be operating. Customers may still be buying the product or using the service. But inside, the builder feels disconnected from the very reason the structure was started in the first place. This is the moment when many people assume the problem must be marketing, strategy, pricing, or market conditions. They search for a better system or a new tactic, unaware that the deeper issue lies somewhere far more foundational than any business plan could ever address.
Scripture quietly reveals a principle that applies to every endeavor a person builds in this world. The Psalmist wrote that unless the Lord builds the house, the builders labor in vain. That statement is not merely poetic language meant to inspire reflection. It is a spiritual law that operates beneath the surface of every human effort. When a person sets out to construct something meaningful, whether it is a family, a ministry, or a business, the strength of that structure ultimately depends on the foundation beneath it. A house built on sand can appear stable for a long time. The walls may be straight, the roof may be strong, and the interior may even look impressive. Yet the unseen weakness beneath the structure guarantees that when storms arrive, the collapse will be inevitable. Jesus described this principle in one of His most famous teachings when He spoke about two builders who constructed their houses in very different ways. One built on rock and the other built on sand, and the difference between them was not visible on calm days. The difference only became obvious when the winds rose and the rain began to fall.
Christian businesses often begin their journey on the Rock, but over time the builder can slowly drift into constructing additional layers on something far less stable. The pressure to succeed can quietly push a person toward relying more heavily on personal intelligence, networking ability, marketing creativity, and financial resources. None of those things are inherently wrong, but they become dangerous when they begin to replace the deeper reliance on God that once defined the mission. A Christian entrepreneur can unknowingly begin operating as though the success of the company ultimately depends on their own effort, their own planning, and their own ability to outwork every obstacle. This shift in perspective rarely feels rebellious. In fact, it often feels responsible. After all, business owners are taught that success requires discipline, planning, and relentless work. But the spiritual danger lies in the subtle transformation that occurs when a calling slowly becomes a personal burden instead of a shared partnership with God.
Many believers reach a point in their business journey where they begin to sense that something is not right. The joy that once accompanied the work has faded. Prayer becomes shorter and less frequent. Time in Scripture feels rushed or postponed because there is always another urgent task demanding attention. The heart that once burned with purpose now feels tired, and the business that was meant to serve as a vessel for faith now feels like a weight pressing down on the soul. This is often the moment when entrepreneurs begin searching for solutions in the wrong places. They attend conferences, purchase new training programs, hire consultants, redesign their brand, and experiment with new marketing strategies. Some of those efforts may produce temporary improvement, but they rarely address the root issue that is quietly weakening the entire structure. The problem is not usually a lack of intelligence or effort. The deeper issue is that somewhere along the journey, the builder forgot who the business truly belongs to.
There is a profound difference between building something for God and building something with God. When people begin their journey with the desire to honor Him, they often imagine themselves constructing something impressive that they will eventually present back to Him as an offering. The intention is sincere, but the mindset can subtly position the entrepreneur as the primary architect of the enterprise. Over time, the builder begins carrying the emotional weight of every outcome, every failure, every financial challenge, and every unexpected obstacle. The pressure grows heavier because the responsibility feels entirely personal. But when a person remembers that God was never meant to be a distant beneficiary of the work, the entire perspective begins to shift. The business was never meant to be an offering constructed independently by human hands. It was always meant to be a partnership where the Creator Himself remains the true builder.
Jesus once told His followers that apart from Him they could do nothing. That statement challenges the deeply ingrained cultural belief that success is primarily the result of human effort. Modern business culture celebrates independence, self-reliance, and personal ambition. Entrepreneurs are often praised for their ability to take control of their destiny and shape their own future through determination and discipline. While those qualities can certainly contribute to achievement, they can also create the illusion that God’s role is limited to providing inspiration while humans handle the real work. The Kingdom of God operates on an entirely different principle. In God’s design, human effort is never meant to replace divine guidance. Instead, it becomes powerful only when it flows from a life that remains deeply connected to Him.
One of the most dangerous moments in the life of a Christian business owner is the moment when success begins to appear. Growth can be far more spiritually risky than failure because it quietly reinforces the belief that the current approach is working. When revenue increases, when recognition grows, and when customers begin praising the value of the product or service, it becomes easier to believe that the system itself is responsible for the results. The entrepreneur may still pray and still speak openly about faith, but the heart can gradually shift toward trusting the structure that has already been built. The danger is not visible immediately because the business may continue thriving for months or even years. Yet beneath the surface, the foundation is slowly becoming disconnected from the Rock that once supported everything.
Eventually the storm arrives. In business, storms can take many forms. Economic downturns can suddenly shrink markets that once seemed stable. Unexpected competition can appear and begin eroding customer loyalty. Internal leadership challenges can disrupt the harmony of a growing team. Personal exhaustion can drain the clarity that once fueled innovation. Sometimes the storm arrives as a quiet sense of spiritual emptiness that cannot be explained by financial numbers or external circumstances. The entrepreneur looks around at the business they worked so hard to build and realizes that something essential is missing. It is at this moment that many Christian entrepreneurs discover a painful truth. The real crisis is not external at all. The real crisis is that the builder slowly drifted away from the One who was meant to be guiding the entire project.
Yet this moment of realization can also become the beginning of something far more powerful than the original vision. When a person recognizes that their foundation has shifted, they are given the opportunity to return to the Rock with deeper humility and clearer understanding than they possessed at the beginning. The rebuilding process does not necessarily mean abandoning the business or starting from scratch. In many cases it means something far more transformative. It means reorienting every decision, every strategy, every ambition, and every measure of success around the presence of Jesus Christ as the true center of the work. It means remembering that the purpose of the enterprise was never simply to generate profit or recognition. The deeper purpose was always to create a vessel through which God’s presence could touch the lives of people who might never step inside a church.
Christian businesses have the potential to become extraordinary instruments of influence in the world. A company led by someone who walks closely with God can create environments where integrity is honored, where employees are treated with genuine dignity, where customers encounter honesty instead of manipulation, and where generosity flows naturally instead of being calculated for public relations. These businesses can quietly reflect the character of Christ in industries that often operate on entirely different values. But this kind of influence only emerges when the builder remains deeply connected to the Source of the vision. When Jesus remains the foundation, the business becomes something far greater than a commercial operation. It becomes a living testimony that faith is not confined to church buildings but can shape every corner of daily life.
The challenge for every Christian entrepreneur is not simply to begin with the right motivation but to remain rooted in that motivation through every stage of growth. This requires something far deeper than occasional prayer or symbolic references to faith. It requires a daily posture of surrender that acknowledges God as the true leader of the enterprise. Decisions must be filtered through prayer rather than made solely through analysis. Success must be interpreted through the lens of spiritual impact rather than financial metrics alone. The entrepreneur must continually remember that the business belongs to God long before it belongs to any human owner. When that truth remains alive in the heart of the builder, the foundation remains secure regardless of how large the structure eventually becomes.
The world does not desperately need more Christian businesses that merely display religious branding. What the world truly needs are businesses led by people whose lives remain anchored in the presence of Christ so deeply that the influence of that relationship quietly shapes every aspect of how the organization operates. These are the businesses where employees sense something different in the atmosphere. They are the companies where integrity is practiced even when it costs money. They are the workplaces where compassion outweighs competition and where success is measured not only by profit margins but also by the lives that are strengthened along the way.
When a Christian entrepreneur remembers the Rock beneath the structure, the entire journey begins to change. Work no longer feels like a lonely struggle to force outcomes into existence. Instead, it becomes a daily collaboration with the One who created the universe and understands the deeper purpose behind every opportunity that appears along the path. The builder no longer carries the entire burden of success because the true Builder has always been present, patiently waiting to guide every step. This realization can transform even the most exhausted business owner into someone who rediscovers the joy that existed at the very beginning of the vision.
The most important rebuilding work in any Christian business does not happen in conference rooms or strategic planning sessions. It happens in the quiet places where a person stands honestly before God and admits that somewhere along the journey the center of gravity shifted. Rebuilding begins when the entrepreneur recognizes that the issue was never primarily about tactics, systems, or market dynamics. The deeper issue was spiritual alignment. A business can be efficient, profitable, and professionally managed while still drifting away from the presence that once gave it life. That drift rarely happens through rebellion. It happens through distraction, through exhaustion, through the gradual accumulation of responsibilities that slowly crowd out the space where prayer and listening once lived. The builder does not wake up one morning and decide to remove God from the foundation. Instead, the foundation slowly becomes buried under layers of activity until the builder begins operating as though everything depends on personal strength alone.
Many Christian entrepreneurs are deeply committed to honoring God, yet they unknowingly fall into a pattern that quietly undermines their own mission. They begin treating spiritual life as something separate from the mechanics of business. Prayer becomes something that happens before the workday begins rather than something that flows through every decision that follows. Scripture becomes a source of inspiration rather than a living guide that shapes leadership choices, hiring practices, partnerships, and financial priorities. The separation is subtle, and it often feels practical because the business world teaches people to rely on measurable strategies rather than spiritual discernment. Over time the entrepreneur begins trusting experience, instincts, and industry knowledge more than the quiet guidance of the Holy Spirit. The business may continue functioning, but the living connection that once made the work feel sacred begins to fade.
This separation is where many Christian businesses unknowingly begin constructing new layers on sand. The structure can appear strong for a long time because human intelligence and discipline are capable of producing impressive results. But eventually every system encounters a moment that exposes the limitations of human control. Markets shift, customers change, competitors innovate, and unforeseen challenges arise that cannot be solved by repeating yesterday’s strategy. When that moment arrives, the entrepreneur discovers whether the foundation beneath the company is truly anchored in Christ or merely decorated with Christian language. The storm reveals what calm seasons can conceal. Businesses that are deeply rooted in the presence of God often navigate storms with surprising resilience because the leader remains anchored in something stronger than circumstances. Businesses that slowly drifted toward self-reliance often feel shaken in ways that expose how fragile the underlying structure has become.
Yet storms are not always destructive. Sometimes they are the very instruments God uses to awaken the builder to a deeper reality. A season of struggle can become a sacred invitation to rediscover the reason the journey began in the first place. Many Christian entrepreneurs describe a moment when their carefully constructed plans stopped working and their sense of control evaporated. In that moment they returned to prayer with a humility that had slowly faded during years of progress. They began asking not merely for success but for guidance. They stopped treating God as someone who blesses their plans and began seeking the plans that God Himself wanted to unfold through their lives. Something remarkable often happens in that moment of surrender. The entrepreneur begins experiencing clarity that does not originate from human calculation. Ideas emerge that align more closely with the deeper calling that first inspired the business.
Rebuilding a business on the Rock does not necessarily mean abandoning ambition or rejecting excellence. In fact, it often leads to a higher standard of both. When Jesus becomes the center of a company’s identity, the entrepreneur begins pursuing excellence not merely to outperform competitors but to honor the One whose name they carry. Integrity becomes more than a policy. It becomes a reflection of the character of Christ. Decisions about pricing, customer relationships, employee treatment, and community involvement begin flowing from a deeper place of conviction rather than short-term advantage. The business gradually transforms into something that reflects the Kingdom of God in quiet but unmistakable ways. Customers may not always be able to articulate what feels different about the company, yet they sense an atmosphere of trust that is increasingly rare in a world driven primarily by profit.
Employees also notice the difference when a business is truly anchored in Christ. Leadership rooted in humility creates environments where people feel valued rather than used. Instead of viewing employees as interchangeable pieces in a productivity machine, the entrepreneur begins recognizing the sacred dignity present in every person on the team. Conversations about goals and performance remain important, but they are balanced by genuine concern for the well-being of the people involved. This shift does not weaken the business. It strengthens it because people tend to give their best work in environments where they know they are respected and appreciated. A company built on the Rock begins reflecting the relational values that Jesus modeled throughout His ministry.
Customers, too, become part of this transformation. In many industries, businesses rely heavily on persuasion techniques designed to maximize sales regardless of whether the product truly serves the customer’s long-term interest. A Christ-centered business approaches these relationships differently. Instead of focusing solely on closing the transaction, the entrepreneur begins asking a deeper question about whether the service genuinely benefits the person on the other side of the exchange. Honesty replaces exaggeration. Transparency replaces manipulation. Trust becomes the most valuable currency the company possesses. Over time that trust often proves more powerful than any marketing strategy because people recognize authenticity when they encounter it.
None of this transformation happens overnight. Rebuilding on the Rock is not a single decision but an ongoing posture of surrender that shapes the rhythm of daily life. It begins with the simple but profound act of remembering who the true owner of the business really is. The entrepreneur may legally hold the title, but spiritually the enterprise belongs to God long before it belongs to any human leader. When that truth becomes real again, the weight of carrying the entire future of the company begins to lift. The builder no longer feels alone in the responsibility because the true Architect is present in every conversation, every opportunity, and every unexpected challenge.
One of the most beautiful discoveries many entrepreneurs make during this rebuilding process is that God often cares about the details of their work far more than they realized. He is not distant from business decisions or uninterested in the practical realities of commerce. The same God who guided fishermen, tax collectors, and craftsmen during the time of Jesus remains present in the ordinary tasks of modern life. When a person invites Him fully into the daily operation of a company, guidance begins appearing in ways that cannot always be explained through conventional logic. Opportunities align at unexpected moments. Relationships form that open new paths forward. Challenges that once felt overwhelming become manageable because the entrepreneur is no longer relying solely on personal strength.
There is also a deeper transformation that occurs within the heart of the builder. When a business is built primarily on human ambition, the emotional highs and lows of entrepreneurship can feel overwhelming. Success brings temporary excitement, but it is often followed by anxiety about maintaining momentum. Failure can feel devastating because it appears to threaten the identity of the person who built the company. When the foundation shifts back to Christ, the emotional landscape begins to stabilize. The entrepreneur discovers that their identity does not depend on the rise and fall of financial results. They remain secure because their life is rooted in something far more enduring than any quarterly report. This freedom allows them to lead with greater courage because their sense of worth no longer fluctuates with the performance of the business.
Many Christian entrepreneurs who experience this transformation begin realizing that their company was never meant to be merely a vehicle for personal success. It was always intended to become a channel through which God could reach people in places where traditional ministry rarely enters. Employees who might never attend a church service encounter leadership shaped by compassion and integrity. Customers who expect ordinary transactions experience unexpected honesty and care. Business partners observe decisions guided by principles that transcend short-term profit. In quiet and often unseen ways, the company begins reflecting the character of Christ to people who may have never encountered Him in any other context.
This perspective changes the meaning of success entirely. Profit remains important because it allows the business to survive and expand its influence, but it is no longer the ultimate measurement of value. The deeper question becomes whether the company is reflecting the heart of God in the way it operates. A smaller business built on that foundation can have far greater spiritual impact than a massive organization that quietly abandoned the Rock beneath its structure. The true measure of success becomes the faithfulness of the builder rather than the size of the building.
For entrepreneurs who feel spiritually dry or stuck, this realization can become the beginning of a profound awakening. The path forward does not require discovering some secret marketing strategy or reinventing the entire business model. The path forward begins by returning to the place where the vision first came alive. It begins by kneeling again in the quiet presence of God and acknowledging that the company was never meant to exist apart from Him. From that moment of surrender, new life can begin flowing through every aspect of the enterprise. The builder rediscovers the joy of working alongside the One who first planted the dream in their heart.
In the end, the greatest danger facing Christian businesses is not competition, economic uncertainty, or limited resources. The greatest danger is forgetting the One they were building it for. When that memory fades, the structure begins slowly drifting away from the foundation that once made it strong. But when the builder remembers the Rock and rebuilds every part of the enterprise upon Him, something extraordinary begins to unfold. The business becomes more than a commercial endeavor. It becomes a living witness that even in the marketplace, the presence of Christ can transform ordinary work into something eternal.
Your friend, Douglas Vandergraph
Watch Douglas Vandergraph’s inspiring faith-based videos on YouTube https://www.youtube.com/@douglasvandergraph
Support the ministry by buying Douglas a coffee https://www.buymeacoffee.com/douglasvandergraph
Financial support to help keep this Ministry active daily can be mailed to:
Vandergraph Po Box 271154 Fort Collins, Colorado 80527
from folgepaula
LIKE A LADY BUG
What I love about Rio is the feeling of untouched alleyways, shaded by generous almond trees, yet the passersby never grab its fruits, perhaps because of the salty winds, or simply out of love for its silence, All the paineiras of Ipanema sit there patiently, protecting all couples in their long, slow kisses, while branches are entertained on their delicate, solitary journey of exploring lightness through the air. Roots know nothing but to seek, to seek; its flowers know nothing but to bloom and give.
There are corners of Rio where the world seems to have stopped in ’95, where the passing of time is measured only by the ice cream cone melting in my hand. Who is born here carries an open heart as destiny, and a gentle indifference toward the rest of the world, poor souls who never tasted this light, the one that rises over the mountains before surrendering itself to the sea.
Here I was born on a sunny spring 1990, my mom couldn't lay down the last two weeks, the umbilical cord is wrapped around the baby's neck, said the doctor: Forget October 11th, she should be born earlier, scheduled September 28th. My mom sat on her bergère in the living room listening to the neighbor playing bossa nova, Tom Jobim that's how I orchestrated my prelude to life. And then just in time for the first flowers to bloom, a week after the beginning of spring, 08:17 of a sunny friday, crescent moon, I had my first breath into the world. My mom dressed me in red and in his first visit, my brother said: “She looks like a lady bug.”
/mar26
from  Roscoe's Quick Notes
Roscoe's Quick Notes

Rangers vs Padres
Listening now to the Padres Radio Network for pregame coverage to be followed by the call of my afternoon's MLB Spring Training Game of choice featuring the San Diego Padres vs my Texas Rangers. Go Rangers!
And the adventure continues.
The Quiet Architecture of Faith: What Hebrews 11 Reveals About the Invisible Life God Is Building
from Douglas Vandergraph
There is something remarkable about the way faith is described in the eleventh chapter of Hebrews, because it refuses to behave the way modern people expect spiritual language to behave. Most people assume faith is primarily about believing certain statements are true, yet the writer of Hebrews speaks about it more like an invisible structure that quietly supports the entire life of a believer. Faith becomes the hidden architecture behind every courageous decision, every act of obedience, and every moment where a human being steps forward into uncertainty while trusting that God already stands in the future waiting. Hebrews 11 opens with a line that has echoed across centuries because it speaks to something deep inside the human spirit: faith is the substance of things hoped for and the evidence of things not seen. That description alone shifts the entire conversation, because it suggests faith is not a fragile emotion or a vague optimism but something substantial, something solid enough to stand on even when the road ahead disappears into fog. In other words, faith becomes the bridge that allows a person to move from the visible present into the unseen future where God is already at work. When the writer of Hebrews begins unfolding example after example from the lives of those who came before, the point is not simply to admire ancient figures but to reveal a pattern that still unfolds in every generation of believers who dare to walk with God.
When you begin to move through Hebrews 11 slowly, you realize the chapter is less like a list of heroes and more like a window into the hidden mechanics of spiritual life. Each person mentioned in the chapter encountered a moment where the visible world offered one conclusion while the voice of God invited them toward another. Abel offered his sacrifice not because he had proof that it would matter but because something within him recognized the quiet authority of God’s presence. Enoch walked with God in such deep alignment that his life itself became a testimony that intimacy with the divine was possible even in a broken world. Noah began constructing an ark in a season where the skies looked perfectly calm, trusting a warning from God about a storm no one had yet seen. Each story reveals a different expression of faith, yet they all share the same underlying rhythm: God speaks, the future shifts, and a human being must decide whether they will move according to what they can see or according to what they trust God is building beyond their sight.
That tension between what can be seen and what must be trusted is where most people struggle, because human nature tends to prefer guarantees before movement. We like to see the full map before we take the first step, and we prefer certainty before commitment. Yet the stories in Hebrews 11 reveal something profoundly different about the way God often leads His people. God rarely provides the entire blueprint at the beginning. Instead, He reveals enough to invite obedience, enough to require trust, and enough to transform the person who is willing to walk forward. When Abraham is called to leave his homeland, the instruction does not come with a full explanation of where he is going or how everything will unfold. Abraham is simply invited to go, and the act of going becomes the beginning of a journey that will reshape history itself. Faith, in this sense, is not simply believing that God exists but trusting that His direction is worthy of your next step even when the destination remains hidden.
This idea challenges modern assumptions because many people think faith is meant to eliminate uncertainty, yet the pattern throughout Hebrews 11 suggests something much deeper is happening. Faith does not remove uncertainty from life; it transforms how a person walks through it. The individuals named in the chapter did not receive comfortable circumstances or predictable outcomes. They received a relationship with God strong enough to carry them through unpredictable circumstances. Abraham lived in tents while waiting for a city built by God. Sarah trusted a promise of life in a season where biology itself seemed to argue against hope. Moses chose to align himself with God’s people even though it meant walking away from the comfort and prestige of Egypt’s royal court. Each decision required stepping into a future that could not yet be measured by human logic. Yet over time the pattern becomes unmistakable: whenever someone trusts God deeply enough to obey, something extraordinary begins unfolding beyond the limits of human planning.
One of the most fascinating aspects of Hebrews 11 is the way it describes people who never fully saw the completion of what they believed. The chapter repeatedly reminds readers that many of these individuals died while still holding onto promises that had not yet materialized in their lifetime. At first glance this might seem discouraging, yet the writer presents it as something profoundly honorable. These individuals understood that faith was never about controlling the timeline of God’s promises but about aligning with the story God was writing across generations. They saw themselves as travelers moving toward a greater homeland, citizens of a kingdom that stretched beyond the boundaries of their immediate experience. Because of this perspective, they were able to live with a kind of steady courage that did not depend on instant results. Their lives became evidence that faith is not measured by how quickly God fulfills something but by how faithfully a person continues walking with Him even when fulfillment unfolds slowly.
There is also something deeply encouraging about the diversity of the people mentioned in Hebrews 11. The chapter does not present a collection of flawless individuals whose lives were untouched by weakness or failure. Instead, it presents a group of people who were deeply human, often imperfect, sometimes uncertain, yet willing to trust God in moments that required courage. Rahab appears in the chapter despite coming from a background many would have dismissed as disqualifying. Gideon is remembered even though his story includes moments of hesitation and doubt. Samson’s life contained profound flaws, yet he still becomes part of the larger testimony of faith. The message here is subtle but powerful: God does not require perfect people in order to accomplish extraordinary purposes. What He seeks are individuals willing to trust Him enough to step forward when the moment arrives.
Another layer of Hebrews 11 becomes visible when you consider how the chapter reframes the meaning of success in the spiritual life. Modern culture often measures success through visible outcomes such as influence, recognition, or material achievement. Yet Hebrews 11 measures success by something entirely different: alignment with God’s will even when the visible outcome remains uncertain. Some individuals in the chapter experienced dramatic victories, seeing kingdoms conquered and miracles unfold before their eyes. Others endured suffering, imprisonment, and hardship without witnessing the immediate triumph of their faith. Yet the chapter places both groups side by side without diminishing either one. This reveals a profound truth about the life of faith: obedience itself is the victory, regardless of whether the world recognizes it in the moment.
When you read the latter portion of Hebrews 11, the tone becomes almost poetic as the writer describes people who endured incredible trials while remaining anchored in trust. Some were mocked, some were imprisoned, some faced persecution that stretched the limits of human endurance. Yet the chapter does not portray them as defeated individuals. Instead, it presents them as witnesses whose lives testify that faith can remain alive even in the darkest circumstances. The writer uses language that suggests the world itself was not worthy of them, implying that their loyalty to God revealed a deeper reality than anything the surrounding culture could offer. This perspective transforms suffering from something meaningless into something that can carry spiritual significance when it is endured with faith and integrity.
There is a reason Hebrews 11 continues to resonate with believers across centuries, and it is not simply because it recounts historical stories from ancient times. The chapter speaks to a universal human experience: the tension between what we can currently see and what we believe God may be doing beyond our sight. Every generation faces moments where obedience requires courage and where trust must extend beyond immediate understanding. When someone chooses to act with integrity in a world that rewards shortcuts, that is an act of faith. When someone forgives despite deep wounds, believing that God can bring healing where bitterness would only deepen the pain, that is an act of faith. When someone continues serving others even when recognition never arrives, trusting that God sees every quiet sacrifice, that too becomes part of the same legacy described in Hebrews 11.
Faith, then, becomes something far more dynamic than many people imagine. It is not merely an internal belief system but a living force that shapes the way a person walks through the world. Faith alters decisions, reshapes priorities, and changes how someone interprets both success and failure. It creates the courage to begin building something before there is visible proof that the effort will succeed. It produces the patience to keep walking through seasons where progress appears slow or invisible. And perhaps most importantly, it allows a person to recognize that their life is part of a much larger story unfolding across generations.
When the writer of Hebrews reflects on the lives of those who came before, the tone carries a quiet reverence because these individuals understood something essential about their place in God’s unfolding plan. They recognized that the visible world is only part of reality and that God’s purposes often develop in ways human eyes cannot immediately perceive. Because of this understanding, they were able to live with a kind of freedom that did not depend on controlling every outcome. They trusted that God’s promises were trustworthy even when the timeline stretched beyond their expectations. In doing so, they left behind a testimony that continues inspiring believers centuries later.
The deeper you reflect on Hebrews 11, the more you begin to realize that the chapter is not only about people who lived long ago. It is also about the kind of life that remains possible today for anyone willing to trust God with similar courage. Faith still invites people to step beyond the comfort of certainty and into the adventure of obedience. It still calls individuals to build, to serve, to forgive, and to hope even when circumstances appear uncertain. And just like the lives recorded in Hebrews 11, the quiet acts of faith taking place today may become part of a legacy that future generations look back upon with gratitude.
As Hebrews 11 continues to unfold in the mind of the reader, the chapter begins to reveal something even more profound than a list of faithful lives. It slowly becomes clear that what we are witnessing is not merely a gallery of spiritual accomplishments but the gradual unveiling of a spiritual pattern that transcends time. The individuals described throughout the chapter did not know they were becoming part of a sacred narrative that would inspire generations thousands of years later. They were simply responding to the voice of God as it intersected their ordinary lives. In the moment, their choices likely felt personal, uncertain, and even risky. Yet from the vantage point of history, their faith appears almost architectural, like beams quietly supporting a structure far larger than any one life could fully comprehend. Hebrews 11 therefore invites us to reconsider how we understand our own decisions of faith today, because what may appear small in the moment can become part of a much larger spiritual legacy over time.
One of the most powerful realizations that emerges from the chapter is that God often works through people who cannot yet see the full scale of what their obedience will produce. Abraham did not know that his journey of trust would eventually shape entire nations and become central to the story of redemption. Moses could not have imagined that his willingness to confront Pharaoh would echo across millennia as a symbol of divine deliverance. Rahab likely never dreamed that her courageous act of protection would place her name within the lineage that eventually leads to Christ. Each of these lives demonstrates that faith often begins with a step that seems modest when viewed from the inside. Yet when God breathes purpose into that step, it can ripple outward through time in ways no human mind could calculate.
This is where Hebrews 11 begins to speak directly into the heart of anyone who has ever wondered whether their faithfulness in daily life truly matters. Many people imagine that spiritual significance belongs only to those who perform dramatic acts that are publicly recognized. Yet the rhythm of Hebrews 11 suggests something different. Faithfulness is not defined by how visible an action becomes but by how deeply it aligns with the direction God has placed within the heart. The quiet decision to trust God when circumstances look uncertain carries a spiritual weight that cannot be measured by immediate results. Over time, those quiet decisions accumulate into something powerful, shaping both the life of the individual and the world around them in ways that often become visible only much later.
There is also a beautiful paradox woven throughout Hebrews 11 that reveals the mystery of how God works through human history. The chapter repeatedly shows people who were moving toward promises they did not fully see fulfilled during their lifetime. They walked forward believing that God’s word was reliable even when the final outcome remained beyond their personal horizon. In a culture that often demands immediate results, this kind of faith can feel almost radical. Yet the writer of Hebrews presents it as the very essence of spiritual maturity. Faith is not merely the ability to believe when the outcome is already visible. It is the courage to remain steady when the outcome remains hidden, trusting that God’s purposes unfold across a timeline larger than any individual life.
When we begin to look at the broader sweep of Scripture through this lens, an incredible pattern starts to appear. God often plants seeds of promise in one generation that will only reach their full expression in another. Abraham receives the promise of descendants as numerous as the stars, yet he experiences only the earliest glimpse of what that promise will become. David establishes a kingdom that points toward something greater, a kingdom that will ultimately find its fulfillment in Christ centuries later. The prophets speak of redemption that will unfold long after their own voices fall silent. Hebrews 11 reminds us that these lives were not defined by how quickly they saw fulfillment but by how faithfully they aligned themselves with God’s unfolding story.
For modern believers, this realization can completely transform the way we view our place in the world. Instead of feeling pressured to produce immediate visible outcomes, we begin to understand that our role may simply be to plant seeds of obedience that God will nurture over time. Faithfulness in parenting, integrity in work, kindness toward others, courage in moments of moral decision, and devotion to God in private prayer may seem ordinary on the surface. Yet when those actions are rooted in trust, they become part of a larger spiritual ecosystem where God continues shaping history through human lives. What appears ordinary in the moment may become extraordinary in the long arc of God’s work.
Another remarkable dimension of Hebrews 11 lies in its emphasis on movement. Faith is rarely portrayed as a static state of belief but as something that propels people forward. Abraham goes. Moses leaves. Noah builds. Rahab protects. Each story contains action, risk, and motion. This reminds us that faith is not meant to exist merely as an internal conviction. It is meant to move through a person’s life in ways that influence decisions, relationships, and the direction of the future. Faith becomes the catalyst that turns spiritual insight into lived reality.
There is also something deeply reassuring about the fact that many of the people mentioned in Hebrews 11 were far from perfect. Their lives contained complexity, mistakes, and moments of weakness. Yet the chapter does not dwell on those failures. Instead, it focuses on the moments when they trusted God enough to move forward. This perspective offers a powerful encouragement to anyone who has ever felt unqualified to walk closely with God because of past mistakes. Hebrews 11 quietly reminds us that faith does not require a flawless record. It requires a willing heart that continues to turn toward God even after stumbling.
The closing verses of the chapter introduce an idea that is both mysterious and deeply hopeful. The writer explains that all these individuals, though commended for their faith, did not receive the fullness of what had been promised because God had something better in store that would ultimately include those who came later. This statement reveals that the story of faith is not a collection of isolated lives but a single unfolding narrative that stretches across generations. Every believer who walks with God becomes part of that same living story. The faith of those who came before strengthens those who follow, and the faith of those living today will quietly influence those who come after.
This generational dimension of faith may be one of the most powerful insights Hebrews 11 offers. When someone chooses to trust God, they are not only shaping their own life but also contributing to a spiritual inheritance that will extend beyond them. A parent who models humility, forgiveness, and trust in God plants seeds that will grow within the hearts of their children. A teacher who encourages faith and integrity influences students who will carry those values into the future. A leader who acts with courage and compassion creates ripples that extend far beyond the immediate moment. In this way, faith becomes a living legacy that quietly multiplies across time.
Perhaps the most beautiful realization that emerges from Hebrews 11 is that faith ultimately points beyond itself to the character of God. The reason these individuals were able to trust so deeply was because they had encountered a God who had proven Himself trustworthy. Faith is not blind optimism; it is confidence rooted in the nature of the One who speaks. The stories in Hebrews 11 remind us that God’s promises have always been larger than human expectations, unfolding in ways that often surpass what anyone initially imagined. When people choose to trust Him, they step into a relationship with a God who is capable of bringing life from barrenness, deliverance from oppression, and redemption from even the darkest circumstances.
In our own time, the invitation of Hebrews 11 remains just as alive as it was for the first readers of the letter. The world still presents moments where people must choose between what appears immediately safe and what aligns with God’s deeper direction. Faith continues to call individuals to walk paths that require courage, patience, and trust. The difference is that today we look back and see the long history of those who have already walked this road before us. Their lives form a kind of spiritual cloud of witnesses, reminding us that the journey of faith has always been filled with both challenges and extraordinary moments of grace.
When you pause and reflect on the entire chapter, you begin to see that Hebrews 11 is not simply describing the past. It is extending an invitation. It invites each reader to imagine what their life might look like if they trusted God with the same quiet courage displayed by those who came before. It invites believers to live with the awareness that every decision of faith becomes part of a story much larger than the present moment. And it invites us to remember that even when we cannot see the full outcome of our obedience, God is already weaving those choices into the future He is preparing.
Faith, then, becomes more than belief. It becomes participation in the unfolding work of God in the world. Every act of trust, every step of obedience, and every moment where a person chooses hope instead of despair becomes another thread in the tapestry God is weaving through history. Hebrews 11 reminds us that the visible world is only part of reality and that God continues working in ways human eyes cannot always see. Yet those who trust Him become participants in that unseen work, building something eternal through lives of faith.
In the end, the message of Hebrews 11 is both humbling and empowering. It humbles us because it reveals that we are part of a story that began long before us and will continue long after we are gone. Yet it also empowers us because it shows that our faith today truly matters within that story. The quiet choices to trust God, to love others, to pursue righteousness, and to walk faithfully through uncertainty all become part of the same legacy described in Hebrews 11. Just like those who came before, we may not fully see the final outcome of our obedience. But we can trust that the God who guided their lives continues guiding ours, building something beautiful across generations through the steady courage of faith.
Your friend, Douglas Vandergraph
Watch Douglas Vandergraph’s inspiring faith-based videos on YouTube: https://www.youtube.com/@douglasvandergraph
Support the ministry by buying Douglas a coffee: https://www.buymeacoffee.com/douglasvandergraph
Financial support to help keep this Ministry active daily can be mailed to:
Vandergraph Po Box 271154 Fort Collins, Colorado 80527
Yakshit Shetty Sued Kwantlen Student Association (KSA)
from  ksaleaks
ksaleaks
The litigation between the Kwantlen Student Association and Yakshit Shetty (LinkedIn) was reported on in the Runner on February 14 2026.
The following are the public court documents which can be accessed by anybody in Canada.
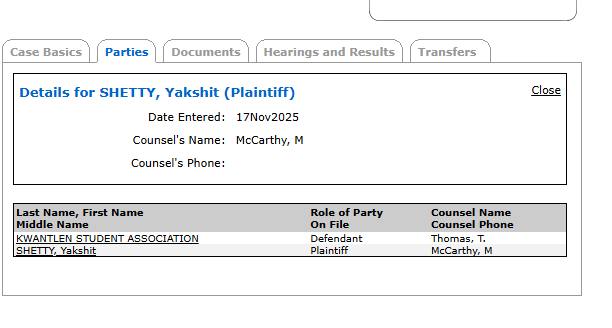
Notice of Civil Claim












Response To Civil Claim











Reply





We will be releasing the court documents of the two other (254775, 250796) cases reported in the same story. Stay tuned!
The Greatest Parable Ever Lived: Seeing the Life of Jesus as the Story God Wrote in Flesh
from Douglas Vandergraph
When most people open the New Testament, they immediately think about the parables Jesus told. They remember the story of the prodigal son, the good Samaritan, the mustard seed, the lost sheep, the vineyard workers, and the wise and foolish builders. These stories are powerful because they contain truths that unfold slowly inside the mind of the listener. Jesus used simple images drawn from everyday life so that eternal realities could be understood by ordinary people. Farmers understood seeds. Shepherds understood sheep. Families understood loss and reconciliation. The genius of the parables is that they slip quietly past the defenses of the mind and land directly in the heart. Yet there is something remarkable that many people miss, even after reading the Gospels for years. The greatest parable Jesus ever revealed was not one He spoke. The greatest parable was the life He lived.
This realization changes the way a person reads the entire Gospel narrative. Instead of seeing isolated events, miracles, teachings, and confrontations, the reader begins to see a single unfolding story that carries meaning beneath the surface of every moment. A parable is a story that reveals a deeper truth through imagery and experience. When viewed this way, the life of Jesus becomes the most powerful illustration of the kingdom of God ever presented to humanity. His birth, His upbringing, His interactions with ordinary people, His confrontations with power, His suffering, His sacrifice, and His resurrection all function together as one living message. It is as if God decided that the clearest way to reveal His heart to the world was not through abstract philosophy or complicated theology, but through a human life lived in perfect alignment with divine love. Jesus did not merely explain the kingdom of God. He demonstrated it with every step He took.
The parable begins in a way that immediately challenges the assumptions people often carry about power, greatness, and significance. The Son of God does not enter the world surrounded by wealth, influence, or political authority. Instead, He arrives in the quiet vulnerability of a newborn child laid in a manger. The King of Heaven begins His earthly life in a feeding trough designed for animals. This is not a random historical detail. It is the opening line of a story that reveals something profound about the nature of God’s kingdom. The world typically associates greatness with visibility, privilege, and status. Yet the first chapter of Jesus’ life overturns that entire expectation. God begins His greatest act of redemption in the most humble setting imaginable. The message quietly embedded in that moment is unmistakable. In the kingdom of God, greatness does not begin with elevation above others. It begins with humility that willingly enters the ordinary spaces of human life.
The location of Jesus’ birth also speaks into the deeper meaning of the parable. Bethlehem was not the center of political power. It was not the seat of religious influence. It was a small town that most of the world would have overlooked. Yet it became the stage where the most significant life in human history began. This detail reveals something about how God often works within the human story. Divine purpose frequently emerges in places the world ignores. Heaven does not depend on human recognition in order to accomplish its plans. The life of Jesus begins as a quiet reminder that God’s greatest movements often start in hidden places before the world realizes what is unfolding.
As Jesus grows from infancy into adulthood, the parable continues through the rhythm of His early life. The Gospels tell us surprisingly little about those years, but what we do know is deeply meaningful. Jesus grows up in Nazareth, a town that carried little prestige in the eyes of the broader culture. In fact, when people later heard that Jesus came from Nazareth, their response revealed the town’s reputation. They openly questioned whether anything good could come from such a place. This reaction tells us something about the cultural expectations of the time, but it also reinforces the deeper theme unfolding in the story. God once again chooses a setting that the world would not consider impressive. The Savior of humanity grows up in a place that many people dismiss.
Yet Jesus does not spend His life trying to escape that background or argue against it. He does not chase recognition or demand that people acknowledge His significance. Instead, He lives quietly, working as a carpenter, participating in the rhythms of everyday life within His community. This long season of obscurity carries meaning that becomes clearer when the entire life of Jesus is viewed as a parable. Thirty years pass before His public ministry begins. Thirty years of ordinary living precede three years that would change the course of human history. This ratio alone speaks to a truth that many people struggle to accept. The preparation of a life often takes far longer than the public expression of its purpose.
Modern culture tends to celebrate immediate visibility and rapid success. People often assume that meaningful impact must appear quickly and dramatically in order to matter. Yet the life of Jesus reveals a very different pattern. The majority of His earthly life unfolds quietly, away from public attention. Those years are not wasted time. They are part of the story God is telling. The silence of those decades reminds us that spiritual formation, character development, and deep alignment with God’s will often happen in hidden seasons that the world does not notice. The parable of Jesus’ life teaches that obscurity does not diminish purpose. In many cases, it prepares a person to carry that purpose faithfully.
When the moment finally arrives for Jesus to begin His public ministry, the story takes a decisive turn. He steps into the Jordan River to be baptized by John the Baptist. At that moment something extraordinary happens. The heavens open, the Spirit descends, and a voice from heaven declares that Jesus is the beloved Son in whom God is well pleased. This event marks the beginning of a ministry that will reveal the heart of God to the world in ways people had never seen before. Yet even here, the parable continues speaking. Before Jesus performs a single miracle, before He gathers disciples, before crowds begin to follow Him, His identity is affirmed by the Father. The order matters. His worth is established before His works begin.
This moment contains a powerful lesson that resonates far beyond the historical event itself. In the life of Jesus, identity precedes activity. The Father declares who Jesus is before the world sees what Jesus will do. The deeper meaning embedded in this moment challenges a pattern that many people fall into throughout their lives. Human culture often encourages people to build their identity through achievement, recognition, or accomplishment. Yet the life of Jesus reveals a different foundation. True identity flows from relationship with God rather than from external validation.
After His baptism, Jesus enters the wilderness for forty days. This part of the story carries profound symbolic meaning within the larger parable. The wilderness represents a place of testing, solitude, and spiritual confrontation. During this time Jesus faces temptation that challenges the very mission He has come to fulfill. The enemy attempts to redirect His path by offering shortcuts to power and recognition. Each temptation represents a distortion of the kingdom Jesus came to reveal. The offer of immediate authority, miraculous spectacle, and self-serving power stands in direct contrast to the path of humility, sacrifice, and obedience that defines His mission.
Jesus refuses every shortcut placed before Him. In doing so, He reveals something essential about the nature of God’s kingdom. The kingdom does not advance through manipulation, spectacle, or domination. It advances through faithfulness to truth even when the path appears difficult. The wilderness becomes another chapter in the living parable of Jesus’ life, demonstrating that obedience to God’s will often requires resisting the temptations that promise quicker success at the cost of deeper integrity.
When Jesus begins traveling throughout Galilee and beyond, the public begins to witness the unfolding message of His life. Crowds gather because something about Him is different from anything they have experienced before. His teaching carries authority that religious leaders struggle to explain. His words cut through confusion and speak directly to the deepest questions people carry. Yet the most powerful dimension of His ministry lies not only in what He says, but in how He lives among people.
Jesus consistently moves toward those whom society has pushed to the margins. He touches lepers who were considered untouchable. He speaks with women whom cultural norms often silenced. He welcomes children who were rarely given importance in public spaces. He sits at tables with tax collectors and sinners whose reputations made them unwelcome in respectable circles. Every one of these interactions becomes part of the living parable unfolding before the eyes of the world.
Through these actions Jesus reveals that the kingdom of God operates according to a completely different value system than the structures of human society. In the world’s system, people are often categorized according to status, wealth, influence, or moral reputation. But in the kingdom Jesus embodies, every person carries immeasurable value because they are created and loved by God. His willingness to cross social boundaries and extend compassion where others withheld it reveals the heart of divine grace.
The miracles of Jesus also function as powerful illustrations within the parable of His life. When He restores sight to the blind, the moment carries both physical and spiritual meaning. The healing reveals that the kingdom of God brings light into places where darkness once dominated. When He raises the dead, the miracle becomes a sign that life in God’s kingdom ultimately overcomes death itself. When He feeds thousands with a small amount of food, the act demonstrates that divine provision can multiply what appears insufficient.
These miracles are not random displays of supernatural power. They are signs that point toward a deeper reality. Each one reveals something about the nature of the kingdom Jesus came to establish. The miracles function like windows through which people can glimpse the future restoration God intends for creation. They offer a preview of a world where suffering, brokenness, and scarcity will no longer have the final word.
As the story continues to unfold, Jesus also confronts the religious structures of His time. His critiques are not aimed at faith itself, but at systems that have lost sight of the compassion and justice that lie at the heart of God’s character. He challenges leaders who place heavy burdens on others while neglecting mercy. He exposes hypocrisy that prioritizes outward appearance over inner transformation. These confrontations become another essential element of the living parable. They reveal that genuine faith cannot be reduced to ritual or performance. True devotion to God must reflect the love and integrity that define God’s own nature.
Through all of these moments, a consistent pattern emerges. The life of Jesus continuously reveals what the kingdom of God looks like when it takes visible form within the world. Every conversation, every healing, every act of compassion, and every challenge to injustice contributes another layer to the story God is telling through His Son.
And the most profound chapters of that story are still ahead.
As the ministry of Jesus progresses, the deeper meaning of the living parable begins to sharpen. What initially appears to be a teacher traveling from town to town gradually reveals itself as something far more profound. People begin to sense that they are not simply hearing wisdom; they are witnessing a life that embodies the very character of God. The more closely someone observes the way Jesus moves through the world, the clearer the message becomes. He does not react the way people expect. He does not pursue influence the way leaders normally do. He does not gather followers in order to elevate Himself. Instead, His authority grows through humility, His influence spreads through compassion, and His power becomes visible through service. These patterns are not accidental details within the Gospel narrative. They are essential elements of the parable that His life is revealing.
One of the most striking aspects of Jesus’ life is the calm strength that consistently surrounds Him. In moments where others panic, He remains steady. In situations where conflict intensifies, He answers with wisdom rather than aggression. There is a composure within Him that seems to come from a place far deeper than circumstance. This composure becomes another living illustration of what life looks like when it is fully anchored in trust toward God. A powerful example appears when the disciples find themselves caught in a violent storm while crossing the sea. Experienced fishermen begin to fear for their lives as the waves crash against the boat. In the middle of this chaos, Jesus sleeps. That image alone communicates something extraordinary about the kind of peace that flows from complete confidence in the Father. His rest in the middle of the storm becomes a living message that faith is not the absence of difficulty but the presence of trust that runs deeper than fear.
As Jesus continues His ministry, the tension between the kingdom He represents and the systems of power surrounding Him grows more visible. Religious authorities become increasingly uncomfortable with His influence. Political structures begin to sense that His message carries implications far beyond spiritual reflection. Yet Jesus never seeks confrontation for its own sake. Instead, He continues revealing the kingdom of God through compassion, truth, and unwavering commitment to the mission He has received from the Father. The deeper the story unfolds, the clearer it becomes that the parable of His life is moving toward a moment where its meaning will be revealed with unmistakable clarity.
That moment arrives in the final days of His earthly life. The events leading up to the crucifixion contain layers of symbolism that bring the entire living parable into focus. The Last Supper, the betrayal by Judas, the prayers in the Garden of Gethsemane, the trials before religious and political leaders, and the suffering that follows all contribute to the climax of the story God is telling through the life of His Son. In these moments the contrast between the kingdom of God and the systems of the world becomes impossible to ignore.
When Jesus kneels to wash the feet of His disciples during the final meal they share together, the message of the parable becomes profoundly clear. In the cultural context of that time, foot washing was a task reserved for servants. It was a role associated with humility and low status. Yet the one they call Lord and Teacher takes that position willingly. He kneels before those who follow Him and performs an act of service that overturns their understanding of leadership. Through this action Jesus demonstrates that greatness in the kingdom of God is measured not by how many people serve you but by how willingly you serve others. The living parable now speaks with unmistakable clarity. Divine authority expresses itself through sacrificial love.
The hours that follow reveal the cost of that love. Jesus is betrayed by one of His own disciples, abandoned by others who fear for their safety, and handed over to authorities who are determined to silence Him. False accusations surround the trials that take place before religious leaders and Roman officials. Yet even as these events unfold, the composure that has characterized His life remains present. He does not lash out in anger or attempt to manipulate the situation for self-preservation. Instead, He continues walking the path that leads toward the cross.
The crucifixion stands as the central moment within the entire parable of Jesus’ life. To many observers in that moment, it appears to be the tragic end of a promising teacher. The Roman cross was designed to communicate humiliation, defeat, and public shame. Yet within the deeper story God is telling, the cross becomes the ultimate revelation of divine love. Every element of the scene carries meaning that transforms the understanding of power, justice, and redemption.
As Jesus hangs on the cross, He speaks words that echo through history with astonishing clarity. Instead of calling for vengeance against those who crucify Him, He asks the Father to forgive them. This moment reveals the heart of God more clearly than any theological explanation could. The living parable reaches its most powerful expression as love responds to hatred with mercy rather than retaliation. In that moment the kingdom of God stands in direct contrast to the cycles of violence that often dominate human history.
The cross also reveals something profound about the nature of sacrifice. Throughout history people have attempted to reach God through acts of devotion, ritual, and moral effort. Yet the story unfolding at Golgotha reveals a different movement. Instead of humanity climbing upward toward God, God descends into the deepest suffering of humanity in order to bring redemption. The cross becomes the point where divine love meets human brokenness in its most painful form. Within the parable of Jesus’ life, this moment demonstrates that the heart of God is willing to enter the darkest places of human experience in order to bring restoration.
For those who witnessed the crucifixion, it appeared that the story had reached its end. Darkness covered the land, and the body of Jesus was placed in a tomb carved into rock. The silence of those hours must have felt overwhelming to those who had placed their hope in Him. Yet the parable of Jesus’ life was not finished. The final meaning of the story had not yet been revealed.
Three days later the resurrection transformed the understanding of everything that had taken place. The empty tomb became the declaration that death itself does not hold ultimate authority over the purposes of God. The resurrection revealed that the sacrifice of the cross was not defeat but victory expressed through love. In the context of the living parable, this moment completes the story in a way that reshapes human understanding of hope itself. The message becomes clear. No darkness is powerful enough to overcome the life that flows from God.
When the disciples encounter the risen Jesus, their fear turns to courage and their confusion turns to clarity. They begin to understand that the life they have witnessed over the previous years was not simply a remarkable human story. It was the revelation of God’s kingdom entering the world through the life of His Son. The living parable they had watched unfold was now entrusted to them as a message to carry forward.
This realization continues to shape the lives of believers throughout history. When people read the Gospels and begin to see the life of Jesus as the greatest parable ever lived, the implications reach far beyond intellectual understanding. The story invites each person to reflect on how the values revealed through the life of Jesus might shape their own journey. His humility challenges the pursuit of status. His compassion challenges indifference toward suffering. His courage challenges fear in the face of injustice. His sacrifice challenges the instinct to protect self-interest above all else.
The parable of Jesus’ life also carries a deeply encouraging message for those who feel that their own lives may be ordinary or unnoticed. When the story of Jesus is viewed as a whole, it becomes clear that many of its most meaningful chapters unfolded in quiet places. The majority of His life took place outside the spotlight of public recognition. Those hidden years were not meaningless. They were part of the preparation for everything that would follow. This pattern reminds us that God often works through seasons that appear quiet on the surface but are shaping a deeper purpose beneath.
Understanding the life of Jesus as a living parable also invites people to see their own lives within a larger story. The same God who revealed His heart through the life of His Son continues to work through human lives today. Acts of compassion, forgiveness, courage, and faith become small reflections of the kingdom that Jesus embodied. Each moment where love triumphs over bitterness or hope rises above despair becomes another expression of the story that began with the life of Christ.
The world continues to face challenges that can easily produce discouragement. Conflict, injustice, suffering, and uncertainty often dominate the headlines of each generation. Yet the parable of Jesus’ life reminds us that the ultimate direction of the story is not determined by human failure but by divine redemption. The resurrection stands as the enduring declaration that hope has the final word in the story God is writing.
When someone begins to see the life of Jesus in this way, the Gospel narrative transforms from a distant historical account into a living invitation. The parable that Jesus lived calls people to walk in the same spirit of love, humility, and trust that defined His journey. It calls them to believe that God continues to work within the ordinary moments of life to reveal extraordinary grace.
The greatest parable ever told was not spoken beside a hillside or inside a synagogue. It was lived step by step through a human life that revealed the heart of heaven. The birth in Bethlehem, the quiet years in Nazareth, the healing of the broken, the courage to speak truth, the sacrifice of the cross, and the triumph of the resurrection together form a story that continues to transform lives across generations. The life of Jesus remains the clearest picture humanity has ever seen of what the kingdom of God looks like when love becomes visible.
And that living parable continues to echo through every life that chooses to walk in the light of that same love today.
Your friend, Douglas Vandergraph
Watch Douglas Vandergraph’s inspiring faith-based videos on YouTube https://www.youtube.com/@douglasvandergraph
Support the ministry by buying Douglas a coffee https://www.buymeacoffee.com/douglasvandergraph
Financial support to help keep this Ministry active daily can be mailed to:
Vandergraph Po Box 271154 Fort Collins, Colorado 80527
from  Kroeber
Kroeber
#002304 – 19 de Setembro de 2025
O meu cubo 5x5x5 caiu no chão e desmanchou-se. É uma metáfora para algumas partes da minha vida. Assim, meio desmontado, nem sequer se põe a questão de ser ou não possível resolvê-lo. Antes de sequer o tentar, há-que lhe devolver estrutura, algo que não sei se consigo aprender.
from  Kroeber
Kroeber
#002303 – 18 de Setembro de 2025
Scavengers Reign faria Mœbius (Jean Giraud) orgulhoso. É uma das obras de animação que melhor segue a tradição visual iniciada por Giraud. Nesta série se vê como o estilo contém já em si todas as cintilações narrativas, o que é visual não é mera ilustração, ou forma de um qualquer conteúdo, é antes o próprio conteúdo visível, manifestado.
Isaiah 43–44
from  wystswolf
wystswolf
Dead gods tell no tales, only the True and Living God's name will endure forever. No marketing required.
Now this is what Jehovah says, your Creator, O Jacob, the One who formed you, O Israel:
Do not be afraid, for I have repurchased you. I have called you by your name. You belong to me.
When you pass through the waters, I will be with you, and through the rivers, they will not flood over you. When you walk through the fire, you will not be scorched, nor will the flame singe you.
For I am Jehovah your God, the Holy One of Israel, your Savior. I have given Egypt as a ransom for you, Ethiopia and Seba in exchange for you.
For you became precious in my eyes. You were honored, and I have loved you. So I will give people in place of you and nations in exchange for your life.
Do not be afraid, for I am with you. I will bring your offspring from the east and gather you together from the west. I will say to the north, “Give them up!” and to the south, “Do not hold them back. Bring my sons from afar and my daughters from the ends of the earth, everyone who is called by my name and whom I created for my own glory, whom I have formed and made.”
Bring out a people who are blind, though they have eyes, and who are deaf, though they have ears.
Let all the nations assemble in one place, and let the peoples be gathered together. Who among them can tell this? Or can they cause us to hear the former things? Let them present their witnesses to prove themselves right, or let them hear and say, “It is the truth.”
“You are my witnesses,” declares Jehovah, “yes, my servant whom I have chosen, so that you may know and have faith in me and understand that I am the same One. Before me no God was formed, and after me there has been none.
I—I am Jehovah, and besides me there is no savior.
I am the One who declared and saved and made known when there was no foreign god among you. So you are my witnesses,” declares Jehovah, “and I am God. Also, I am always the same One, and no one can snatch anything out of my hand. When I act, who can prevent it?”
This is what Jehovah says, your Repurchaser, the Holy One of Israel:
For your sakes I will send to Babylon and bring down all the bars of the gates, and the Chaldeans, in their ships, will cry out in distress.
I am Jehovah, your Holy One, the Creator of Israel, your King.
This is what Jehovah says, the One making a way through the sea and a path through turbulent waters, the One who draws out the war chariot and the horse, the army together with the mighty warriors:
They will lie down and not get up. They will be extinguished, snuffed out like a burning wick.
Do not remember the former things, and do not dwell on the past.
Look! I am doing something new. Even now it is springing up. Do you not recognize it?
I will make a way through the wilderness and rivers through the desert. The wild beast of the field will honor me, the jackals and the ostriches, for I provide water in the wilderness, rivers in the desert, for my people, my chosen one, to drink, the people whom I formed for myself so that they might declare my praise.
But you have not called on me, O Jacob, because you grew weary of me, O Israel.
You have not brought me sheep for your whole burnt offerings or glorified me with your sacrifices. I have not compelled you to bring me a gift, nor have I made you weary by demanding frankincense.
You did not buy me sweet cane with your money, and with the fat of your sacrifices you did not satisfy me.
Instead, you have burdened me with your sins and made me weary with your errors.
I, I am the One who is blotting out your transgressions for my own sake, and I will not remember your sins.
Remind me; let us bring our case against each other. Tell your side of it to prove you are in the right.
Your first forefather sinned, and your own spokesmen have rebelled against me.
So I will profane the princes of the holy place, and I will give Jacob over to destruction and subject Israel to insulting words.
Now listen, O Jacob my servant, and you, O Israel, whom I have chosen.
This is what Jehovah says, your Maker and the One who formed you, who has helped you from the womb:
Do not be afraid, my servant Jacob, and you, Jeshurun, whom I have chosen.
For I will pour out water on the thirsty one and flowing streams on the dry ground. I will pour out my spirit on your offspring and my blessing on your descendants.
They will spring up among the green grass like poplars by the streams of water.
One will say, “I belong to Jehovah.” Another will call himself by the name of Jacob. Yet another will write on his hand, “Belonging to Jehovah.” And he will adopt the name of Israel.
This is what Jehovah says, the King of Israel and his Repurchaser, Jehovah of armies:
I am the first and I am the last. There is no God but me.
Who is there like me? Let him call out and tell it and prove it to me. From the time I established the people of long ago, let them tell both the things to come and what will yet happen.
Do not be in dread, and do not become paralyzed with fear. Have I not told each of you beforehand and declared it?
You are my witnesses. Is there any God but me? No, there is no other Rock. I know of none.
All who form carved images amount to nothing, and their cherished objects will be of no benefit. As their witnesses, they see nothing and know nothing, so those who made them will be put to shame.
Who would form a god or cast a metal image that can bring no benefit?
Look! All his associates will be put to shame. The craftsmen are mere humans. Let them all assemble and take their stand. They will be terrified and be put to shame together.
The metalsmith works the iron over the coals with his tool. He forms it with hammers, working it with his powerful arm. Then he grows hungry and his strength fails. He drinks no water and grows tired.
The wood-carver stretches the measuring line, tracing out the pattern with red chalk. He works it with a wood scraper and traces it with a compass. He patterns it after a man, with the beauty of a man, to sit in a house.
There is one whose work is to cut down cedars. He selects a certain type of tree, an oak, and he lets it grow strong among the trees of the forest. He plants a laurel tree, and the rain makes it grow.
Then it becomes fuel for a man to make fires. He takes part of it to warm himself. He builds a fire and bakes bread. But he also makes a god and worships it. He makes it into a carved image and bows down before it.
Half of it he burns up in a fire. With that half he roasts the meat that he eats and is satisfied. He also warms himself and says, “Ah! I am warm as I watch the fire.”
But the rest of it he makes into a god, into his carved image. He bows down to it and worships it. He prays to it and says, “Save me, for you are my god.”
They know nothing, they understand nothing, because their eyes are sealed shut and they cannot see, and their heart has no insight.
No one reflects in his heart or has understanding, saying: “Half of it I burned up in a fire, and on its coals I baked bread and roasted meat to eat. Should I then make the rest of it into a detestable thing? Should I worship a block of wood from a tree?”
He feeds on ashes. His own deluded heart has led him astray. He cannot save himself, nor does he say, “Is there not a lie in my right hand?”
Remember these things, O Jacob, and you, O Israel, for you are my servant. I formed you, and you are my servant. O Israel, I will not forget you.
I will blot out your transgressions as with a cloud and your sins as with a thick cloud.
Return to me, for I will repurchase you.
Shout joyfully, you heavens, for Jehovah has acted! Shout in triumph, you depths of the earth! Shout for joy, you mountains, you forest and all your trees!
For Jehovah has repurchased Jacob, and on Israel he displays his splendor.
This is what Jehovah says, your Repurchaser, who formed you since you were in the womb:
I am Jehovah, who made everything. I stretched out the heavens by myself, and I spread out the earth. Who was with me?
I frustrate the signs of the empty talkers and make diviners act like fools, confounding the wise men and turning their knowledge into foolishness.
I make the word of my servant come true and completely fulfill the predictions of my messengers.
I say of Jerusalem, “She will be inhabited,” and of the cities of Judah, “They will be rebuilt, and I will restore her ruins.”
I say to the deep waters, “Be evaporated, and I will dry up all your rivers.”
I say of Cyrus, “He is my shepherd, and he will completely carry out all my will.”
I say of Jerusalem, “She will be rebuilt,” and of the temple, “Your foundation will be laid.”
SMK rhymes with Mastodon
from  SMK - Statens Museum for Kunst
SMK - Statens Museum for Kunst
OK, maybe not phonetically. But for a museum dedicated to open access, a decentralised, non-algorithmic social media platform seems an obvious place to make ourselves available and claim a space for the national Danish art collection.
 A mastodon (well, some sort of mammoth) figurine visiting SMK
A mastodon (well, some sort of mammoth) figurine visiting SMK
Last week, on an early spring Friday, we took our first baby steps into the Fediverse, the collection of platforms connected by the ActivityPub protocol. We did this by setting up an account on the cosy Danish expressional.social server populated by friendly-seeming natives (with an endearing love of image alt texts).
Now, that previous paragraph contains the words ‘protocol’ and ‘server’ and admittedly the Fediverse does require some acclimatisation: it’s just a slightly more abstract concept than your average centralised service. But such is the price of openness and flexibility. When you can “do” the Fediverse almost any way you please, choose your own server and choose your own app, things immediately become a bit complicated.
Slightly technical as it may be, it’s also very promising. The early adopters stand ready to help, all the features (and more) that you may want from a Twitter/X-like platform are available and the non-algorithmic focus imparts a feeling of control. On Mastodon you may be slightly confused, but you’re also very much in charge.
Of course, what you’re not getting is content going viral to a massive audience. Mastodon is thinly populated at this time. So we’re decidedly not there for the reach but because we see clear affinities with our openness ambitions, because the platform’s open architecture may allow for really interesting re-use/automatisation and because there might be a time where the current social media behemoths lose steam. In which case our mastodon riding skills may well come in handy.
We’re starting small. But we see great potential – not least for joining forces across museums and other fine cultural institutions. French cultural institutions are getting together at ReseauCulture.fr – and perhaps Danish/Nordic ones should look very closely at that model. Hit us up if you’d like to talk! 🤗
🏠 SMK on Mastodon (we speak Danish)
 Our first Mastodon post
Our first Mastodon post
La guerre
from  Turbulences
Turbulences
Je n’ai jamais connu la guerre. Je suis issu d’une génération privilégiée. Né au bon moment. Né au bon endroit.
Mes parents l’ont connue.
Mon père, né en 1939, ne pouvait pas savoir, au moment de fêter son cinquième anniversaire, ce que c’était que la paix.
Ma mère, née en 1944, a bien failli ne pas être ma mère. Ses frères et sœurs, dans leur précipitation, l’ont une nuit oubliée en courant se réfugier dans la cave. Les bombes ne sont pas tombées loin, une armoire a basculé sur son berceau. Ils étaient solides les berceaux, en ce temps là.
Comme tant d’autres de sa génération, mon père est allé en Algérie. On ne lui a pas demandé son avis… Il en est revenu, lui.
Je suis né quelques années après.
Mes grand parents ont connu deux guerres. Mes arrières grands parents ont connu deux guerres. Je pourrais continuer longtemps comme ça, si je le voulais.
Je l’ai dit : génération privilégiée.
Et pourtant…
Même si je n’ai pas connu la guerre, même si je ne l’ai pas vécue dans ma chair, ce que j’en sait me suffit largement.
Mais la guerre n’est pas un choix.
On fait la guerre- par défaut – parce qu’il est trop tard – parce que les autres options sont épuisées – parce que les décisions qu’il aurait fallu prendre à temps n’ont pas été prises – parce qu’à un moment le courage à manqué.
Parce que les puissants ont manqué de courage. Parce qu’ils n’ont pas su écouter. Parce qu’ils croyaient savoir. Parce qu’ils étaient bien trop arrogants pour reconnaître qu’ils s’étaient trompés.
Alors ils en envoient d’autres se faire tuer.
C’est compliqué la paix.
Ça demande du courage, de l’écoute, du respect.
Alors que c’est si simple la guerre.
Il y a les gentils, il y a les mauvais.
Et puis, il y a tant d’argent à gagner…

Chapter 5: The Gnochemist
from A Romantasy for Guys and Men
Chapter Index ARFGAM contains mature themes and at times is #NSFW
After leaving Michelle, Stelmaria and Chad were having a conversation about whether she should make herself known to his family. Surprisingly, Chad's position was the logical one. Unsurprisingly, Stelmaria would convince him to agree to her position. This conversation was long, repetitive, and boring. Luckily, more interesting things were happing on ethereal side of reality.
***
Sebastian whistled at his workbench and chipped away at the piece of petrified wood. Making petrified wood chips was the one simple alchemical task he had never assigned to an assistant. He found it relaxing. His boss Trinity had a long standing complaint that it was 'a simple task way below his pay grade'. Since Sebastian knew all she would ever do about it is tell him in performance reviews that his refusal to allocate this task was 'beyond unacceptable and incredibly petty,' so he cheerfully ignored her complaints.
Sebastian had been working as an alchemist at the Ethereal Alliance Tranquility Council's Office of Courageous, Kind, & Laudable Interdisciplinary Civilian Knights that Virtuously and Ardently Guarantee the Terrific Omnipresent Civilized Utopia is Maintained for decades. Growing up Sebastian had been sure of two things. The first was that he wanted to be an alchemist. The second was that his family was too poor to afford the admission fees for an alchemical school. As a result he pursued an Alliance program that would cover his education in exchange for ten years of government service following its completion. When he first learned he had been assigned to the Knights, he assumed the ten years of service would be miserable. By year five he had come to realize that he loved being a knight.
Three years after this realization that he met his spouse, Taylor. They were an heir to a sizable family fortune dating back to pre-Alliance times. When they proposed to him it made the decision on if he should leave the Knights for a higher paying job when his required service was complete, an easy one.
Now at the age of sixty-seven, he found himself as both the Chief of Alchemy and Assistant Director, Field Force Support. The latter of which he had become because fifteen years prior when the AD2FS who had been his primary mentor retired, Sebastian informed Giovanni, the Knight Director, he did not want to report to “whoever he thinks can do the job justice”. Giovanni, agreed that Sebastian could report directly to him. Sebastian loved this arrangement because the Knight Director has l zero time to spend managing the Chief of Alchemy.
Eight years later Giovanni retired. The current Knight Director, Trinity, succeeded him. Unfortunately for Sebastian, Trinity happened to be the AD2FS that he had refused to report to. The first thing Trinity said to Sebastian after being named Knight Director was “I have an amazing opportunity for you.”
Sebastian hated the administrative bullshit that went with being AD2FS, but cared about the Knight's mission enough to do a good chunk of it. He did all the stuff he thought was actually necessary for the success of the mission. He skipped all the dumb bureaucratic stuff like attending departmental budget reviews or Trinity's weekly leadership meetings.
Sebastian had been making petrified wood chips for the last six hours. It was one of his days off. He was stressed. If the mission had gone remotely well, Des would have been back yesterday. At thirty and three Despoina was the youngest Field Knight in the twelve millennia of the Knight's existence to be named Regnar-Leas, the highest field rank. In Sebastian's opinion, she was on her way to being the greatest Knight the Alliance would ever see. Still, he disagreed with her and Trinity's decision to send her on this mission solo. The delay in her return was all the proof he needed that he was right.
Chipping the petrified wood was the only thing keeping him from imagining how he was going to explain to Taylor that a Massena Escapee brutally murdered their little sister and was most likely harvesting souls in Tempo to try and grow in power because she had been raised in a cult dedicated to reestablishing the ancient Seelie Court and murdering all fiends as well as any älva and kodoma subtypes traditional folklore tends to associates with the Unseelie. It was not a conversation he wanted to have with his spouse.
The chunk he was working on had been as big as his head at the start of the day, it was now smaller than his thumb. He did not have any more, and he knew it. His hearts were an anxious tick-thunk, tick-thunk, like a pair of drums in his chest. When the steady beat was interrupted by the screech of his office door swinging open, he was so surprised he nearly fell off his stool.
The hand that smacked a pile of silver coins down on his desk was covered in dry blood and mud, but there was purple paint on its long pointy finger-nails. Sebastian felt every one of his muscles relax. There was one more tick-thunk and then he only heard his sister-in laws heavy breathing. He spun on his stool and jumped into her arms.
“What you are not going to gloat?” Des managed to say, she sounded exhausted.
Gloat? Sebastian was not sure what she could possibly be talking about. “I have been chipping petrified wood for hours Des. I thought I was going to be telling Tee about your brutal execution by a lunatic. I would have made Trinity tell your parents though.”
“Well now I am a bit disappointed. I guess surviving means that I lost my bet to you and that Trinity gets to avoid a conversation she would have hated.”
“What did the boss say when you gave her your report?”
“Errrrr, I do not know. I have not seen her yet. I just got back.”
“Despoina, why in the Arcanum did you not send a report ahead? This was critical-CRITICAL shit. I told you time and again the samples I looked at suggested that Stelmaria may be the strongest hyōsei to exist in this age. Trinity has probably been preparing a report for the Tranquility Council since yesterday morning assuming...” Sebastian chuckled and leaned onto his young sister in-law. “Fuck Des, even I would not dare to fuck with the boss that much. Does it make me a bad AD that I am proud? Rhetorical question, I do not care if I am a bad AD that would be Trinity's fault for being petty and promoting me.”
Sebastian looked up at Despoina's face for the first time. There was not a hint of amusement in her face which was strange because fucking with Trinity was pretty much the only thing that made his sister in-law smile. “You are being earily quiet Des, keep it up and I will call you 'Little Si...Ouch”
“I may be about to collapse you shithead but I am not deaf. Nobody calls me that but the one sibling I still talk to. That includes that one sibling's husband who I regrettably have to interact with as part of my job. I am juiced. Alchemical. Blood. Right. Now. Before. I. Decide. To. Drink. Yours.”
Sebastian rolled his eyes at that. “Des I know, you know that gnome magic cannot be harvested even by a pterafri sucking our blood. I also know you do not even eat fish because you do not want to be like your parents. Why do you need Alchemical? You will have enough time to spend sleeping with a bloodstone before Trinity assigns you something knew. The side effects can be pretty bad if it is not made right you know?”
“Seb, I did not get her. She escaped...with a human.”
“Are you fucking with me?”
Despoina covered her face with her hands and shook her head. “He shot me, in the eye, with an iron tipped wooden arrow.”
“GAHAHAHAAHAAAHAAAAA,” Sebastian fell to the floor laughing. He knew it was wrong but a puny human besting his sister in-law with a human made weapon was the most ridiculous thing he had ever heard. “Sorry, sorry, sorry I know this is serious this is just...what are the odds? Arcane shit. It had to be pure iron Des its the only way right? Fuck that is impossible and then the shaft was wood? Fuck, do you know most human weapons have not been made out of pure iron in centuries?” Sebastian, took a deep breath. “Sorry, I am sorry this is serious.”
He got up and grabbed a key ring out of his pocket and unlocked a small silver chest sitting on his work bench. “I made some yesterday afternoon when you had not returned. Just in case. There are exactly three fairies in the known realm that could make a better substitute for the real thing. I am not saying there will not be side effects but I am saying I feel pretty confident none of them will be permanent.” He held up a large glass phial about half the size of a bottle of wine. It was filled with a thick maroon cream.
Despoina snatched the phial out of his hand, popped open the lid and sniffed it. “How many times have you made Alchemical Blood Sebastian?”
Sebastian watched sweat pool on Des' brow as she examined his work. “Yesterday was the first, second, third, and fourth times I have made Alchemical blood. I destroyed the first two due to lack of color uniformity, which some studies have linked to more extreme crashes. The third I feared was rather low in potency based on arcane readings so I destroyed that one after I made this one, which is the fourth. As I said there might be a handful of fairies that could do better.”
Sebastian crossed his arms and smirked as he added, “It costs a small fortune to make a single phial, the entire annual alchemical supply budget the council gives me would have been wiped out by what it cost me to make these four. I bought the ingredients with your family's money. I told Taylor you had a mission that was dangerous enough I wanted to have some special ingredients outside of the Council's budget just in case you came back with something that would otherwise be very painful to treat.”
Des grimaced, “did they buy that?”
“Nope. They said to tell you that craving blood is a part of who you are and does not make you your mother.”
“I am going to gut that fucking fur ball for making me do this,” Despoina vowed. Then she tilted her head back, lifted the phial to her lips, and slammed it back in three giant gulps. It was sickly sweet. “Not as disgusting as your mint flavored memory salve, but a close second.”
She turned and walked out the door. Magically mending and cleaning her soiled clothes with a wave of her hand on her way out.
***
Meanwhile back in the temporal side of reality Stelmaria had eventually gotten Chad to agree with her by offering him a boob job. He was now passed out on his bed snoring loudly. Stelmaria said a quick chant to make sure her cute bean would stay asleep while she was out hunting. Then jumped out his bedroom window, shifted into her beast form, and trotted off towards town.
AUTHOR's NOTE: The reader is likely to notice that as we explored the Ethereal Alliance's civilization that the there are abbreviations, acronyms, and slang was common. Some of these readers may be thinking something akin to 'So I am just supposed to accept that this fantasy world is based in the English language and Latin alphabet or that somehow their wordplay can translates seamlessly to ours in a way that sometimes creates puns in English by coincidence?' For these readers I would like to offer two different explanatory responses for them to choose from.
OPTION A: Of course not, the language and alphabetS in the world our story is set in in more fantastical and complex than most could comprehend (but not you because you are so brilliant and smart). There writing system was a combination of logographic, phonetic, syllabic, and enigmatic characters (some pictorial and some abstract). The cleanness of the abbreviations has only been added here to make reading easier for less intelligent readers. If this is breaking your immersion I apologize and if there is ever a super deluxe sprayed edged limited premium edition collector's copy, rest assured I pay to have it written in an original language that only people as smart as you can understand.
OPTION B – “Are you aware that most of the worlds languages use acronyms, abbreviations, and slang? That even some of the ancient languages used them? The ancient Greeks and Ancient Romans used both acronyms and abbreviations. I looked it up and there are examples of abbreviations in ancient Mayan written language as well (which I only selected as my example because my (high school level) understanding of ancient history is the Mayans were isolated from Eurasia and Africa until the sixteenth century). I am not an expert on classic literature (also high school level understanding) but I think there are thgere puns in Beowulf, the Illiad/Odyssey, and One Thousand and One Nights? One thing I know for sure is both testamets of the christian bible have wordplay. What was the point of this author's note? No you are not supposed to even think about that so you should not have to accept it. As stated in the forward this story is poorly written. I sincerely apologize if this is a pet peeve of yours and my decision to do this has mad you sad. Let me try to move your mood in a different direction. Despite spending winters alone in the middle of the ocean, Atlantic Puffins are monogamous and mate for life. They come back to the same nest with the same partner year after year. Its like an annual second chance romance or lost lovers or something. How fun!”
#Romantasy #RomantasyforMen #Satire
from Faucet Repair
9 March 2026
Face shield bag (working title): was walking in Vauxhall and found the outer packaging for a set of CPR mannequin shields. Made of transparent plastic, on which was printed a wonderfully-poorly-rendered line drawing diagram showing how to use the product—hands affixing a shield to a mannequin's lifeless face, another (living?) face entering the diagram's second stage to put its lips to the first one. All folded in on itself and resting delicately over sparse weeds sprouting from wet soil squeezed up against a concrete curb. Something about it brought to mind Polke's watchtower series (particularly Watchtower (Hochsitz) from 1984), both in mood—relaxed at a kind of equilibrium but sinister—and visual complexity—the bent plastic packaging caught daylight at odd angles, blocking visibility of the weeds, soil, and diagram here and there. What resulted is a painting that to me feels ancient, like a hieroglyph partially lost to material decay. Which sits in an odd harmony with the satisfaction on the face floating at the top of the composition. The color is indebted to Eliot Porter's Winter Wren, Great Spruce Head Island, Maine (1960), which holds an aspirational kind of long-ago-now-ness that I'm permanently searching for.
2026-03-09
from Two Sentences
A whole day incident at work, my favorite. I did get praise from upper management though— yippee.