Want to join in? Respond to our weekly writing prompts, open to everyone.
Ray Bradbury, prophet
Ray Bradbury's 1957 book Dandelion Wine is a tale of small town Midwestern America through the eyes of a 12-year old boy. I picked it up after re-reading the more well-known Something Wicked This Way Comes, which comes after Dandelion Wine in the trilogy.
Yesterday, I read through the chapter on the 'Happiness Machine' that Leo Auffmann sets out to make. The idea hits him like a bolt of lightning, and he becomes obsessed on creating a machine that will bring people happiness. Interestingly, his wife (and others) don't see the need for such a device. After a frightening encounter with one of their children and the machine, Leo's wife Lena wants to try it out. Leo and the children hear her crying from outside the machine. Puzzled by the experience, here is Leo and Lena's conversation when she comes out:
“Oh, it's the saddest thing in the world!” she wailed. “I feel awful, terrible.” She climbed out through the door “First, there was Paris...” “What's wrong with Paris?” “I never even thought of being in Paris in my life. But now you got me thinking: Paris! So suddenly I want to be in Paris and I know I'm not!” “It's almost as good, this machine.” “No. Sitting in there, I knew. I thought, it's not real!” “Stop crying, Mama.” She looked at him with great dark wet eyes. “You had me dancing. We haven't danced in twenty years.” “I'll take you dancing tomorrow night!” “No, no! It's not important, it shouldn't be important. But your machine says it's important! So I believe! It'll be all right, Leo, after I cry some more.” “What else?” “What else? The machine says,'You're young.' I'm not. It lies, that Sadness Machine!” “Sad in what way?” His wife was quieter now. “Leo, the mistake you made is you forgot some hour, some day, we all got to climb out of that thing and go back to dirty dishes and the beds not made. While you're in that thing, sure, a sunset lasts forever almost, the air smells good, the temperature is fine. All the things you want to last, last. But outside, the children wait on lunch, the clothes need buttons. And then let's be frank, Leo, how long can you look at a sunset? Who wants a sunset to last? Who wants perfect temperature? Who wants air smelling good always? So after awhile, who would notice? Better, for a minute or two, a sunset. After that, let's have something else. People are like that, Leo. How could you forget?” “Did I?” “Sunsets we always liked because they only happen once and go away.” “But Lena, that's sad.” “No, if the sunset stayed and we got bored, that would be a real sadness. So two things you did you should never have. You made quick things go slow and stay around. You brought things faraway to our backyard where they don't belong, where they just tell you, 'No, you'll never travel, Lena Auffmann, Paris you'll never see! Rome you'll never visit.' But I always knew that, so why tell me?”
While reading this, I couldn't help but think, 'Bradbury prophesied smart phones and social media perfectly!' Lena's experience is the same as legions of others who report dissatisfaction and sadness with their own lives after being drawn in to the fake world of social media. The most poignant observation is, “It's not important, it shouldn't be important. But your machine says it's important! So I believe!”
Online (we don't see the term 'virtual reality' used often any longer) the relationships there aren't real. The experiences aren't real. The only thing seemingly real is the disappointment people face when they look at the reality of their lives against the false creations of Facebook, Instagram, Twitter, and the like. While not as dystopian as Fahrenheit 451, Bradbury saw the bleak future that awaited humanity as we traded the real for the imaginary. He was a genius.
In the remainder of the chapter, the Happiness Machine bursts into flame, destroying itself and the Auffmann's garage. In the aftermath, Leo sits on his front porch looking in to his family going out their ordinary, day-to-day lives and has the epiphany, “There it is...the Happiness Machine.”
Brilliant. Thank you, Mr. Bradbury.
#Bradbury #culture #life #reading
Coding Is Dead, Long Live Programming
from Ian Cooper - Staccato Signals
Summary
In this post, we argue that the role of a coder now belongs to a coding agent, but that the distinct role of a programmer defines the software engineer's role in interacting with the agent to produce computer programs. At the heart of this are, I think, answers to questions we have about software maintenance and the education of junior engineers.
Coding is Dead
Commentators in the tech industry have recently declared that “coding is dead.” The triggers for this statement are:
- LLMs, whose transformer architecture excels at pattern recognition and translation, have achieved a high success rate on key coding tasks, particularly since the December 2025 model releases.
- The improvements in coding agents have pushed the success rate for the code that an LLM generates above the 80% threshold, where agents can begin the journey toward independently doing work without human review for short tasks and increasingly lengthening.
- A wider understanding of good practices in context engineering—using the file system as memory and aggressively managing context by creating fresh agents—has helped prevent the quality drop that comes from context rot.
- The improvement of techniques to capitalize on agents' relentlessness to get them to iterate toward high-quality outputs via clear acceptance criteria for “done-done,” avoiding low-quality output caused by reward hacking. See How To Ralph.
Of course, all statements like “coding is dead” are hyperbolic, but it would be foolish to refute that in 2026 and beyond: agents will write the majority of code.
If coding is dead or will be dead by the early 2030s, what will software engineers do?
Programming is not Coding
The terms programming and coding can seem interchangeable, but historically, they are not the same. They refer to different activities, but for many years we have performed them together, making the distinction unclear.
Following Yourdon and Constantine in Structured Design, we assert that software engineering has the following roles:
- Analyst: talks to the customer to elicit the requirements for what we want to automate.
- Designer: determines how to meet the requirements and required quality attributes of the software, for example, how we split into modules, how those interoperate, scale, provide transactional integrity, etc.
- Programmer: decides on the design of programs: algorithms, data structures, and design patterns – writes coding specifications. QA of the program.
- Coder: implements the program design and has knowledge of syntax.
In the latter two roles, the original distinction between programmer and coder stems from an era when code was often punched out on cards rather than encoded in a high-level language. A programmer handed the coder a coding specification that defined the program to be written:
“Each component subprogram is coded using the coding specifications. Ideally, this phase would be a simple mechanical translation; actually, detailed coding uncovers inconsistencies that require revisions in the coding specifications (and occasionally in the operational specifications).” Bennington, Herbert; Production of Large Computer Programs.
Once, in larger organizations, different people performed the roles of programmer and coder. The programmer specified what code was needed and handed the resulting coding specification to the coder, who then authored the code that was to be loaded into the computer.
With the introduction of high-level languages, it became easier for developers to perform both the programming and coding roles simultaneously. The compiler did much of the work that the coder had done before, so the program specification could be completed simultaneously with coding. Later, the RAD/agile movements leveraged the ease with which programs could be specified as code was written, speeding up software development by collapsing many steps into a single process and shifting quality left via Test-Driven Development.
It is because of high-level languages and RAD/agile practices that many people use “programming” and “coding” interchangeably. But they are not the same.
Coding or Programming: What is the Difference?
You can reason about this difference easily. Once you learn multiple programming languages, you come to appreciate that all of them have variations of the same concepts: control structures, variables, etc., that only differ by their syntax. By contrast, data structures and algorithms don't depend on specific language syntax. Object-Oriented models of your domain can be developed using CRC cards or UML, without writing code. We think of these concepts as existing outside the syntax and the code, at the level of the program. You can reason about a program in a conversation, or on a whiteboard, without needing to use a specific syntax.
When writing code, you probably used to look up what you needed in documentation or examples and translate it to your domain. These statements were code and reusable as such, once fitted to the logic of your program.
We often overestimate the importance of coding in this merger of roles. It is likely that you spend more of your time as a programmer debating which frameworks and libraries you want to use, and what classes and interfaces form part of your model, than you do over whether you should use a for or while loop.
Knowing what syntax to use in a particular language is the role of a Coder; knowing what the code should do is the role of the Programmer.
Alex Booker has a good description of the difference between coding and programming in his video Coding or Programming: What Is the Difference?
XP: Elaboration, CRC Cards, Programming & Coding
Armed with this understanding, it may be helpful to identify when a developer is in a programmer or coder role. Consider the roles we took in an XP-like software development life cycle (SDLC).
- A team takes a story from the backlog and discusses it with the product owner. They develop acceptance criteria. Engineers perform the analyst role.
- The team makes architecturally significant decisions; these may bubble outside the team. Engineers perform the role of the designer.
- Skills like Attribute-Driven Design and Large Scale Domain Driven Design are applied here.
- The team may write an ADR to record architectural decisions.
- The team discusses how to implement the story. They discuss key parts of the domain model, including finding actors, assigning responsibilities to roles, and mapping roles to classes. They talk about the suitability of data structures and algorithms. They perform the role of the programmer.
- As part of this process, the engineers may explore the space with tools like CRC cards.
- The team may write an ADR to record architectural decisions.
- Once the team has a design, they break it into tasks. They perform the role of the programmer.
- They take tasks one by one and pair or mob on them.
- One of the pair uses the keyboard to type code. They are in the coder role.
- One of the pair, or the rest of the mob, specifies what should be written, watches for errors, correlates with the design, and reviews. They are in the programmer role.
The developer roles are: analyst, designer, programmer, coder.
Notice how the coder role is a relatively small part once we break out programmer from it. Because any team member may switch in and out of roles, we overlook how often we are in the programmer role rather than the coder role (or the analyst or designerrole). This tallies with the observation that coding is a small part of what software engineers do and aligns with the reason: many activities are, in fact, programming rather than coding. Your perception of how little of your job is coding is not incorrect, but you perhaps don't appreciate that analysis, design, and programming are engineering activities.
The Middle Loop
In their book Vibe Coding, Steven Yegge and Gene Kim discuss the Middle Loop, the construction of the context the agent uses when carrying out tasks. We often call this specification-driven development, but it bears less resemblance to older document-heavy approaches to software development, and more to the activities of the classic XP loop, with agents in the coding role.
Whilst this is an evolving practice, we can think about a common loop for working with agents like this:
The Middle Loop
- A developer takes a story from the backlog and discusses it with the product owner. They develop acceptance criteria. Engineers perform the analyst role.
- The team may use a PRD to record the requirements.
- The agent may act in a researcher role. The developer may need to make architecturally significant decisions; these may bubble outside the team. The engineer performs the role of the designer.
- Skills like Attribute-Driven Design and Large Scale Domain Driven Design are applied here.
- The agent may act in a researcher role.
- The developer may write an ADR to record architectural decisions.
- The developer decides how to implement the story.
- As part of this process, the engineer and agent explore the space.
- The agent may act in a researcher role.
- The developer performs the programmer role, making decisions with discretion and taste.
They look at key parts of the domain model, finding actors and responsibilities, assigning responsibilities to roles, and roles to classes.
- They talk about the suitability of data structures and algorithms.
- They might use tools like Responsibility Driven Design (RDD).
- As part of this process, the engineer and agent explore the space.
- Once the developer has a design, the agent breaks it into tasks. The developer reviews the tasks, performing the role of the programmer.
The Inner Loop
- The agent takes tasks one by one.
- The agent writes the code. They are in the coder role. The developer watches for errors, correlates them with the design, and reviews. They are in the programmer role.
The Inner Loop The Middle Loop
The developer roles are: analyst, designer, programmer. The agent roles: researcher, coder
The loop is fundamentally the same as XP, but the developer no longer performs the coder role and may be assisted by a researcher role:
The researcher role helps us utilize existing knowledge and patterns more efficiently because the programmer can delegate research that they used to do to the agent.
We didn't previously break out this role; it was part of being a programmer, and it is what we were doing when we visited Stack Overflow, documentation, or pulled candidate objects from the requirements based on their responsibilities.
We might still need to do some of this by reading, but the agent can help with heavy lifting, so we add a new role for that. However, decision-making, based on discernment and taste, lies with the programmer role.
The key, though, is that much is familiar from our first loop. Even with an agent's help, many roles still fall to the human-in-the-loop.
High-Level Direction Judgement and Taste
“It’s not perfect, it needs high-level direction, judgement, taste, oversight, iteration and hints and ideas. It works a lot better in some scenarios than others (e.g. especially for tasks that are well-specified and where you can verify/test functionality). The key is to build intuition to decompose the task just right to hand off the parts that work and help out around the edges.” Andrej Karpathy, x.com
Judgement, taste, etc., are the programmer's responsibilities. The agent is good at coding, but it needs help deciding what to write. That is why we still need the programmer role and don't simply delegate that to the agent. Maybe one day it will do that role too, but that day is not today.
Watch the Loop
Why suggest that the programmer/coder split is like pair/mob programming, where one partner watches the other? Because the agent needs to be observed.
“It's important to watch the loop as that is where your personal development and learning will come from. When you see a failure domain, put on your engineering hat and resolve the problem so it never happens again.
In practice this means doing the loop manually via prompting or via automation with a pause that involves having to press CTRL+C to progress onto the next task. This is still ralphing as ralph is about getting the most out how the underlying models work through context engineering and that pattern is GENERIC and can be used for ALL TASKS.” Geoffrey Huntley, Everything is a Ralph Loop
Now, some argue that it is inefficient. Do you need to review the agent's output? It's just coding. Just use a linter and check that it passes the tests.
Watching the loop confirms the theory behind what you are doing. What is the theory? That's the bit you must come away from the development loop with. It is how you will be able to reason about and maintain the software.
Programming as Theory Building
Peter Naur's essay, “Programming as Theory Building” states that the most important part of programming is theory building: “ On the Theory Building View of programming the theory built by the programmers has primacy over such other products as program texts, user documentation, and additional documentation such as specifications.” The theory, the knowledge built up by the programmer in crafting the program, is important for three reasons:
- The programmer can explain how the program maps to the problem domain: “the programmer must be able to explain, for each part of the program text and for each of its overall structural characteristics, what aspect or activity of the world is matched by it.”
- The programmer can explain the decisions that led to the choices expressed in the program text and documentation.
- The programmer is able to understand how to modify the program to support change: “Designing how a modification is best incorporated into an established program depends on the perception of the similarity of the new demand with the operational facilities already built into the program.”
It is the latter point that is key. In large codebases, our ability to maintain a program depends on our possessing the theory of the program. The theory lets you modify the program successfully because you understand how the program's theory should be adjusted to meet the new requirement.
“The point is that the kind of similarity that has to be recognized is accessible to the human beings who possess the theory of the program, although entirely outside the reach of what can be determined by rules, since even the criteria on which to judge it cannot be formulated.”
The risk is that modifications made to a program, without understanding the theory, lead to decay. Most of us have experienced decay when modifications accrete as new additions that don't fit the theory of the remainder of the program. Eventually, the program becomes incoherent, and we are forced to rewrite.
“The death of a program happens when the programmer team possessing its theory is dissolved. A dead program may continue to be used for execution in a computer and to produce useful results. The actual state of death becomes visible when demands for modifications of the program cannot be intelligently answered. Revival of a program is the rebuilding of its theory by a new programmer team.”
Theory is the key to maintenance. If you don't have the theory, then you will struggle to maintain the software, because you will struggle with the programmer role.
“A very important consequence of the Theory Building View is that program revival, that is, reestablishing the theory of a program merely from the documentation, is strictly impossible.”
Code Reviews and Theory Building
In teams that don't use pair programming, a common compensation is to do code reviews. The purpose of both pair programming and code review extends beyond quality review; it is about sharing the theory of the program.
Often, teams struggle with reviews as flashpoints or have arguments in pairing because they fail to do enough theory-building when they pull the story from the backlog, a process we call elaboration or alignment. A simple way for many teams to improve code reviews is to avoid doing design there but to shift it left into elaboration when the story is pulled from the backlog. This shifts the theory building to an earlier step. The review then just confirms that the code matches the theory. Conflict arises when the theory is unclear during pairing or review.
Pair programming and code reviews spread the theory through the team. Junior developers often don't have the same facility with theory-building that senior developers do. Pairing, or code reviews, allow developers to exchange the theory through conversation and reach alignment.
These exchanges work best when they don't focus on the code but on the theory of the program.
The danger is that a new developer on the team, who has yet to build the theory for the program, in conversation with other developers, correctly specifies the program without the theory. Without the theory, their programming specification is likely to be wrong, and the resulting code will be wrong.
InnerSource, OpenSource, and Theory Building
OpenSource, or InnerSource projects, encounter this need to help contributors acquire theory all the time. Often, Open-source projects identify tasks that require less theory to help new contributors get started. Once contributors establish a track record of contributions, maintainers begin to invest the time in helping them understand the theory.
LLMs and Theory Building
The LLM cannot be used in the analyst, designer, or programmer roles, only as a researcher to support, because it cannot capture the theory of the program as expressed by Naur.
- The LLM does not have the context that lives outside the code, docs, and ADRs.
- The theory cannot be reconstructed only from the artifacts in the git repository [Naur].
- The LLM struggles with large programs. They remain too large for it to hold it all in the conversation and avoid context rot.
As such, an agent struggles to know the theory of the program and fulfill the programmer role. This is why the design is a conversation with the agent. This is why the loop must be observed. Acting as the programmer, you are building the theory of the program.
This, then, is the danger of handing the programmer role to the agent, rather than using it as a researcher. You no longer have the theory of the program, which will lead to the software decaying under modification.
This is why, when working with an agent, it is important to observe the loop, because we need to build the theory of the program. We may choose to work either as a pair programmer, reviewing the test and implementation as they are developed, or as a code reviewer, looking at the PR from the agent. Again, both will be easier if we shift left and put more effort into the design of our program, building a clear theory.
Agents' speed at writing code does mean that the old conflict, in which design insights that update our theory are much more easily applied, persists. With hand-written code, we may resist the amount of work a change to the theory represents for an insight. But with an agent, we just ask the agent to update the design, change the tasks, and add tasks to modify existing code.
Of course, updating the design for a new theory necessitates having tests that confirm the behavior remains the same when we change the theory. This is why we practice TDD. (This is also why we do TDD against behaviors and not details – because we want to be able to revise our theory, not make it rigid).
A Programming Episode with Brighter
As I am writing this, I am working with an agent to pick up a backlog item for Brighter. Configuration for Brighter can be hard. Even for simple CQRS, you need to ensure that pipelines are consistently sync or async, handlers are registered, and when you use messaging middleware, message mappers and transformers, subscriptions and publications, reactor and proactor pipelines, the whole thing has plenty of opportunities to trip users (including agents) up. The “pit of success” for Brighter is a source of a lot of friction and causes developers to reject us in favor of other frameworks.
What we need is static analysis, diagnostics, and dynamic analysis (Roslyn) to help. It looks like a useful backlog item to burn some tokens on.
Working with an agent to fulfill this, once we outline the requirements, requires us to pass our ADR steps.
We use our workflow spec:design to kick this off, and the agent has a pretty good attempt at the design of a tool that would meet the requirements.
But Brighter is a mature codebase, so it gets it wrong. It can't hold all of our code in its context. Its approach isn't dumb; it just misses a lot. It fails to understand the levels at which configuration can occur: local, with producers to the external bus, and with configuration to an external bus.
It doesn't yet have a theory for how to do this.
I give feedback on it. I explain the theory of the levels of configuration. I tell it about IBrighterBuilder and how that can help.
It refines its approach. It's better, but while it recognizes that we need a model of our pipelines, it fails to associate that with using our IAmAPipelineBuilder<T> to create pipelines; instead, it describes (a dry run is what I tell it) and not to build.
I give it more feedback. I explain the theory of using IAmAPipelineBuilder<T> to populate a model that describes a pipeline we can use to validate and report.
We re-run, and now it proposes extending PipelineBuilder with describe methods to build a model. This looks better.
I notice how it is setting up its rules. We have an implementation of the Specification pattern that is already checked in for some future functionality. It is in an assembly that depends on this one, but we can move it and its tests. I discuss it with the agent as a better way to implement this.
This is iterative, a conversation with the agent as we work out the theory of how this fits together. I already hold much of the theory of how Brighter works. I can extend that theory to what might work to implement this feature. The agent can pursue this faster than I can, reading existing code, figuring out what it would take to make it real.
This is programming. We are building the theory of how this works.
Does Stack Matter?
One simplistic idea is that the stack you use does not matter. Now that you can use an agent to write the code, what does it matter what stack you write it in? The problem comes down to whether you can build the theory of the program if you don't understand the stack. In some situations, you may be able to understand the theory without knowing the language, but in other situations, the nuances of how we choose to use language features to represent program theory may be important. Typically, as complexity grows, so does the likelihood that the stack – not just the language but the frameworks and libraries we use – is important to the theory, and as such, we have to understand it.
In cases where we need to understand the stack to build the theory, this would create unmaintainable code in which the programmer does not understand the stack they are working with.
Can LLMs Build Theory?
Agents are continuously new developers who struggle to maintain the theory, even if it is presented to them in conversation. So agents, like new developers, don't have the theory and can be coders but not programmers without supervision.
When using an agent, developers experienced with the codebase may be slower, precisely because they need to explain the theory to the agent. For short tasks, where explaining the theory might take longer than just doing the work, manual efforts may be faster due to this cost.
As codebases expand, we would seem to have increasing issues in codebases where the programmer role has been delegated to the agent, which has no theory, and thus treats every new requirement as novel. This accretes multiple theories into the codebase, which eventually becomes incoherent for agents or people.
New Developers, LLMs, and Theory
This also explains why senior developers are more productive with coding agents:
- They already have the theory, and they can explain it to the agent.
- A new developer does not have the theory and will make mistakes when specifying the program for an agent. Someone who has the theory must thus review the program of a new developer when using an agent, because the new developer does not have it.
Will Agents Develop Theory?
Memory is the key problem for agents with theory, both forgetting the theory behind changes and the amount of context required to keep those decisions in mind when modifying existing code. It's possible that developments in LLMs over time will break down this problem, allowing agents to build and retain theory. For now, the programmer role does seem beyond agents. They can help as a researcher, but don't have the theory a seasoned developer has with a codebase.
For now, then, the programmer role requires a person.
A Programming Episode with Brighter
Reviewing the ADR, the agent wrote, I realize we now have two approaches to validation. One uses our Specification<T> pattern, but the other creates a bespoke validation infrastructure. This seems ugly. If we are moving to the Specification<T> pattern, why do we still have a bespoke class to check our pipeline?
After reviewing the ADR, I realize the issue is reporting failures. Our Specification<T> pattern will give you pass/fail, but won't tell you which rule failed and why. It also explains an earlier issue, where the review noted that we were throwing an error from a Specification<T> when we reached a failure case that should not occur. We need to implement the Visitor pattern in our specification to collate all the errors.
I explain this change to the agent, noting that using the Visitor pattern will allow us to accumulate error messages in the graph, which can be retrieved if the combined specification evaluates to false. I tell the agent to ask me questions so that we can have a dialogue about this design.
The agent tries to overcomplicate this at first. When it answers, it can't figure out how to make this work. At a guess, the model doesn't recognize this approach. It can't initially see how to translate the multiple rule failures from its bespoke code, so it comes up with a ForEachSpecification<T>. I have to walk the agent back to basics on this approach, explaining that each Specification<T> is a rule; a rule may result in multiple breaches, to be recorded in an IEnumerable<ValidationResult>. I then explain that if there are any results, the predicate fails. The visitor pattern is then used to retrieve the results. I suspect that I assumed the agent understood this pattern combination, but it does not.
The agent now understands and presents a summary. The summary matches my expectation, so I ask it to go ahead and change the ADR.
The code looks simpler. I spot some failures to extract methods, leaving a complex implementation. Although this is just an ADR, I will have the agent change it now.
Overall, this conversational process is faster than writing this out by hand. We are getting closer iteratively.
But I also appreciate that I had simply accepted this, without properly reviewing, I would have had something less maintainable, because there were no clear patterns flowing through the code, but different ideas lashed together. I have worked with code bases where new insights had not led to refactoring, resulting in a codebase that felt like a lesson in decision archaeology. That was what would have happened here, without effective review. Because I took on the agent's roles as a researcher and a programmer, we iterate toward a cleaner design.
I feel comfortable spending more time here than I did before. The rush to get to writing code is gone. The agent can handle that quickly. Instead, I iterate on the design, safe in the understanding that the agent can deliver it quickly.
Return of the Programmer
Armed with the understanding that we have merged two roles in our thinking for years, how does this help us think about the future for software engineers?
In the era of agents writing code, this distinction between programming and coding becomes important. With coding agents, the agent is fulfilling the role of the coder at the levels of accuracy that mean it is rapidly taking over that task. But human software engineers continue to own the task of programming. The two have been merged in recent years, but we need to recognize their differences so we can make better decisions about who owns each task.
from The-Wandering-Soul
A little less poetic writing today. Normally I write out what I feel and I sit with it for a few days and buff up the text so it's poetic and impactful.
Not today though. Today I'm just here, as is.
Heading out on a small, day trip to a cool computer parts place. Makes me miss 'Fry's Electronics' but this place is so nice as well.
I'm sitting in the car with my favorite people and I'm tired as hell. Running on 4 hours of sleep.
Traffic is ass, as usual but I'm looking forward to the day.
I do wonder what we are gonna get for lunch... I get car sick on an empty stomach, so I'm planning ahead.
For now, I've got a coffee and a scarfed down my breakfast sandwich.
from Lastige Gevallen in de Rede
Goedemorgen Beste baldur nederland klaagzang interventie medewerker
aangezien ze bij baldur naamloze of besloten gelimiteerd verantwoordelijk voor eigen gedoe handelsmaatschappij hun infomail toch niet echt gaan lezen zet ik de inhoud daarvan hier maar neer. Het vergroot de kans op actie elders zelfs met mijn minimale invloed op alles wat overal op aard koopt en verkoopt en dat aanziet voor leven.
Ik mail u over twee dingen ten eerste de mogelijk spoedige levering van de onlangs bestelde 4 plant producten, is daar sprake van? Ik heb twee bananenplantjes en 6 lelie ballen besteld, bij de wachttijd stond 3 tot 6 dagen. Dit is dag 5 al, nog 2 dagen wachten en god had al een hele bol met inhoud en al geproduceerd, u zou lijkt mij in die tijd wel 6 ballen en 2 jeugdige enthousiaste planten kunnen zetten in een kartonnen doos en dan door een transport onderneming laten afvoeren naar mijn zeer kleine perkje, de mini ruimte die ik mag innemen van het almachtige aanwezige vooral in nummers en dergelijke omgezette taal. Zou u mij kunnen vertellen welke enorm onoverkomelijke problemen u rondom heeft waargenomen om dit vervoer te voorkomen zeg het mij in Yip en Jannuke taal zodat ik ook zie wat u heeft gezien en dan opgelucht adem kan halen, dat is mij al dagen niet meer gelukt.
Ik had wat dit schrijven betreft ook gebruik kunnen maken van het door u waarschijnlijk zeer gewaardeerde antwoord formulier maar dan zou ik daar onder moeten invullen dat ik geen robot ben, als een robot mij vraagt mij of ik er geen ben dan vind ik dat voor weinig woorden veels te erg, zeker ook omdat ik eigenlijk wel een robot oftewel slaaf ben, Ik ben een slaaf van het groot koop systeem, een van u, een dwangmatige klant, net als u lezer aan de andere kant van deze linea, net als degenen verantwoordelijk voor het installeren van die soft en hardware, de enigste niet robots heb ik vijf dagen geleden bij u gekocht. Trouwens op dat slaafse koop moment vroeg niemand daar in u software residerend aan mij of ik een robot was of een vrij alles wat vast zit los kopend mensje, een naturel personage levend in echte natuur, dingen doet gedragen door daglicht, met de hand ipv een karikatuur moeizaam overlevend in een kunstmatig pientere. Zou u deze software makers kunnen vragen om in naam van mij en zeker ook van Albert Einstein, die van de Allee, bij die ene aanklikbare robot vraag een tweede invul vakje te maken waarbij ik mag aangeven dat ik zeker wel een deugdelijke gehoorzame robot ben want dat is namelijk het enigste juiste antwoord op die domme vraag. Dan hoef ik ook niet steeds meerdere keren vier motoren of fietsen of bruggen of trappen of brandkranen of bergen of bussen of auto's of zebrapaden aan te tikken met mijn aan de muis klevende klik hand, van die dingen die alleen een robot doet.
Nutrient Antagonism in Cannabis: Why Chasing Deficiencies Makes Things Worse
from PlantLab.ai | Blog
The Short Version
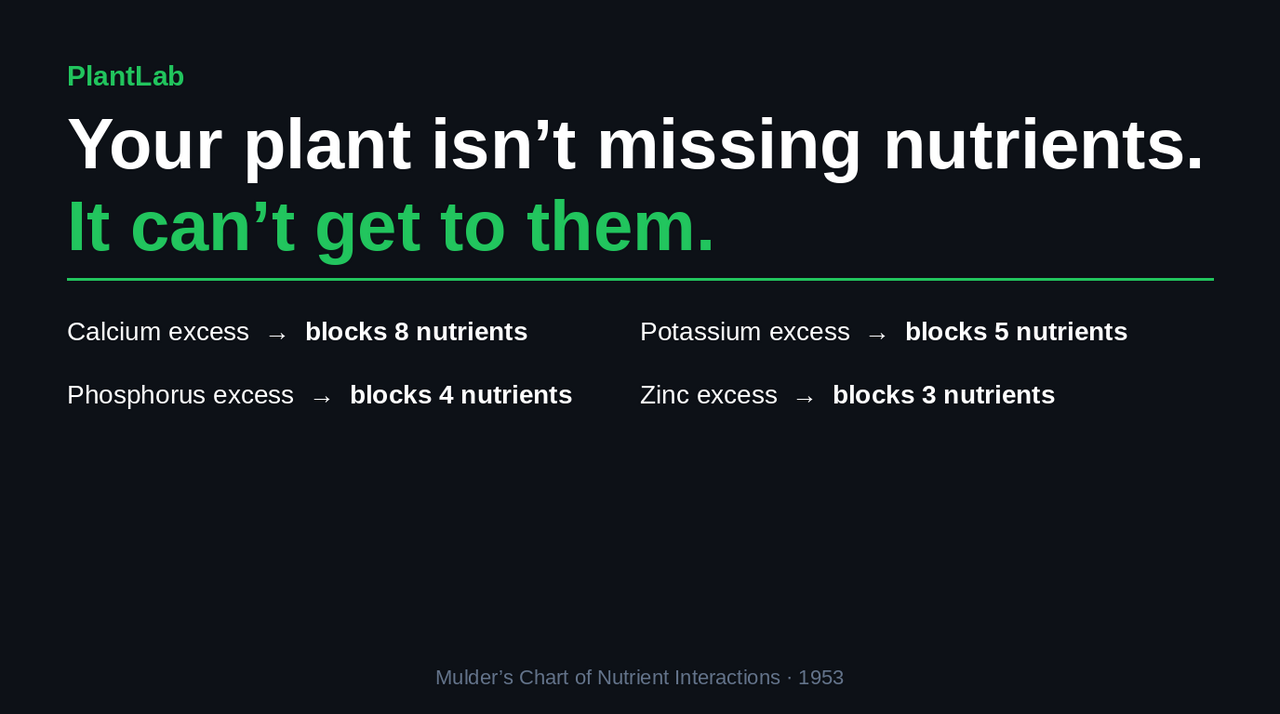
Nutrient antagonism is when excess of one nutrient physically blocks another from being absorbed – your plant has enough of what it needs, it just can't get to it. Adding more of the blocked nutrient usually makes things worse. A 1953 agricultural chart called the Mulder's Chart maps all of these interference relationships; PlantLab's diagnosis now applies that same logic automatically, flagging the most likely excess nutrient in every analysis.
What this post covers: – Why “add more” is sometimes the exact wrong answer – The Mulder's Chart: what it shows and how to read it – The four antagonism traps cannabis growers hit most often – How to tell antagonism from a true deficiency – What to actually do once you've identified the likely excess
You're three weeks into flower. New growth is showing interveinal chlorosis – yellowing between the veins. Classic iron deficiency. You've seen it before. You adjust your pH, add some chelated iron, wait a few days. Nothing. You add more. The leaves get worse. Two weeks of this and your runoff EC looks completely normal. What is going on?!
Here's the thing: your plant probably has plenty of iron. The problem is that something else is blocking it from getting in. You're chasing a deficiency that isn't really there.
That's nutrient antagonism – and it's the reason “add more nutes” is sometimes the exact wrong answer.
Why Adding More Makes It Worse
Plant roots absorb nutrients as ions through specific transport proteins – essentially tiny gates in the root membrane, each specific to particular ions. The problem is that some ions are chemically similar enough to compete for the same gate.
Calcium (Ca²⁺) and magnesium (Mg²⁺) compete directly. Iron (Fe²⁺) and manganese (Mn²⁺) compete. Phosphate and zinc compete. When one is present in excess, it floods the available uptake pathways and crowds out the competition. The blocked nutrient can be sitting right there in your solution at perfectly normal levels – the plant just can't get it through.
Think of it like a packed venue with a capacity limit. Having more people waiting outside doesn't get anyone in if the wrong crowd already filled the room.
Your nutrient solution looks fine on paper. Your runoff TDS is normal. But the plant is effectively starved of the blocked nutrient. When you add more of the blocked nutrient, you're just adding more people to the outside line.
The fix is not to add more of the blocked nutrient – it's to reduce the excess that's doing the blocking.
The Mulder's Chart: 70+ Years of This Being a Known Problem
In 1953, agricultural researcher Cornelis Mulder published an analysis of how essential plant nutrients interfere with each other. The interactions he mapped have been confirmed and refined by plant scientists ever since. Farmers and agronomists have used the resulting chart as a standard diagnostic tool for decades.
Most cannabis growers have never heard of it.
Here's the cannabis-relevant subset, derived from the interaction patterns that show up most in real-world growing:
| If you have excess of... | It blocks uptake of... |
|---|---|
| Calcium | Boron, Iron, Magnesium, Manganese, Phosphorus, Potassium, Sulfur, Zinc |
| Phosphorus | Copper, Iron, Manganese, Zinc |
| Potassium | Boron, Calcium, Magnesium, Nitrogen, Phosphate |
| Nitrogen (toxicity only)* | Boron, Copper, Potassium |
| Zinc | Copper, Iron, Manganese |
| Iron | Manganese |
| Manganese | Iron |
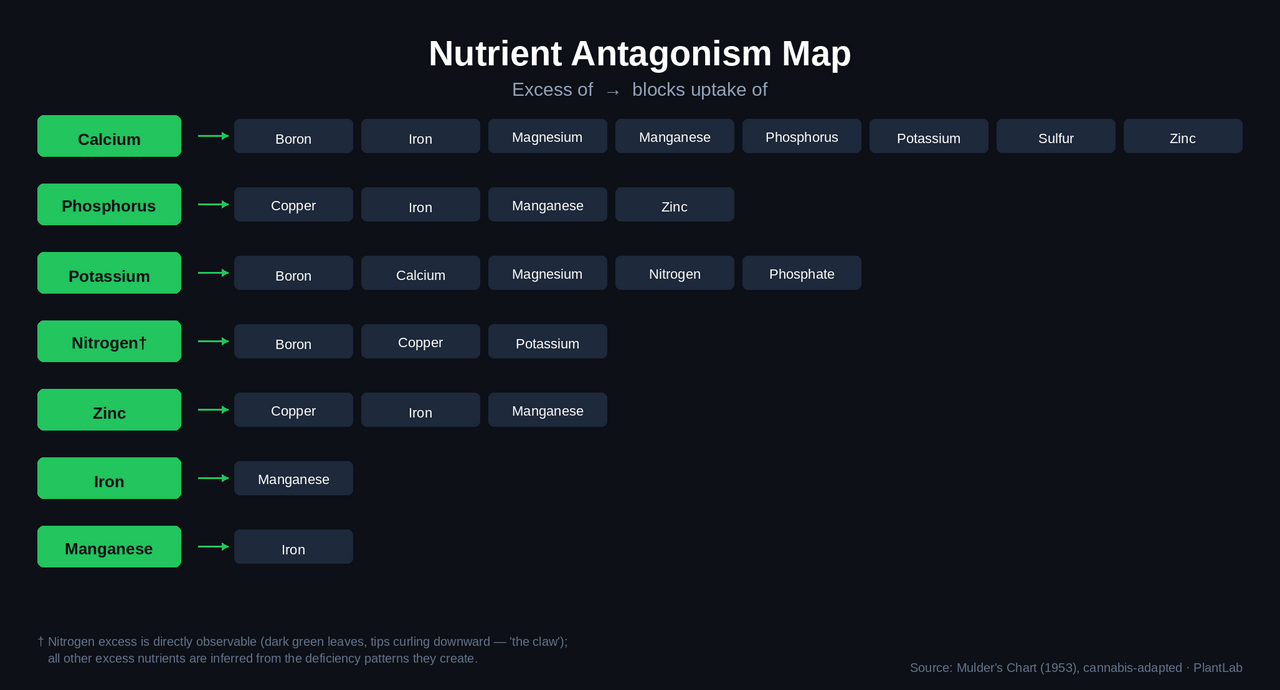
Calcium is the overachiever – it can block uptake of nearly everything else. This is also why CalMag can backfire when calcium is already the problem.
One important distinction about nitrogen: it's the most visually distinctive excess in this table. While every other entry can only be inferred from the deficiencies it creates, nitrogen toxicity has its own unmistakable signature – dark green, shiny leaves with tips curling downward, the “claw.” You can't look at a plant and spot phosphorus excess; you see iron and zinc and manganese deficiency appearing together, and you work backwards from that.
The Four Traps Cannabis Growers Hit Most
The following are the scenarios you'll recognize from forum threads, grow journals, and that one grow that made you seriously question everything.
Trap 1: The Calcium-Magnesium See-Saw
Magnesium deficiency and calcium deficiency share visual overlap in early stages – interveinal chlorosis, lower leaves first. The forum answer is CalMag. CalMag works great when both calcium and magnesium are actually depleted. The problem: if calcium is already elevated (hard tap water, previous CalMag doses stacking, heavy base feed), adding more calcium deepens the antagonism against magnesium uptake. The magnesium deficiency gets worse, you add more CalMag, calcium climbs higher, and you're doing laps around the same problem.
The lesson isn't that CalMag is bad. It's that the same supplement that fixes a true Ca/Mg deficiency actively worsens a calcium-driven lockout.
Trap 2: The Phosphorus Stack
Late veg or early flower: you flush the plant, then hit it with a P-heavy bloom formula to push the transition. Phosphorus accumulates fast. Now iron, zinc, and manganese uptake are all suppressed simultaneously. Three separate deficiency symptoms appearing in the same growth period, on new leaves, none of them responding to treatment – that pattern almost always points to one excess, not three separate missing nutrients.
Trap 3: The Hard Water Baseline
Tap water at 200+ ppm calcium (common in many regions) puts you at or above the antagonism threshold before you've added a single ml of nutrients. Your nutrient line looks balanced on the label, but calcium is already dominating the root zone before the grow starts. By mid-flower, everything from magnesium to iron to zinc is struggling. Check your source water with a TDS meter before spending two weeks blaming your feeding schedule.
Trap 4: Soil Buildup
Amended soil and organic media are forgiving by design – but they accumulate phosphorus and potassium over time. By week 6 or 7 of flower, even a conservative feed is compounding on top of weeks of residual buildup. Micronutrient lockout becomes predictable. If your soil grows have historically gone sideways in late flower despite clean feeding, this is the first thing to look at.
Antagonism or True Deficiency: How to Tell
If the problem is antagonism, adding more of the deficient nutrient won't fix it – and may accelerate the decline. Use these signals to read the situation:
Signs you're probably dealing with antagonism: – You already added the deficient nutrient and symptoms didn't improve or got worse (i.e. stop, just stop!) – The symptom pattern matches a known antagonism pair from the table above (i.e. hey, that's it) – Multiple micronutrient deficiencies appeared at the same time, not sequentially (i.e. why does this happen to me) – Runoff EC/TDS is elevated (i.e. I knew it!) – You've been stacking the same formula for several weeks without a flush or reset (i.e. it worked before, what gives?)
Signs it's probably a true deficiency: – Fresh grow, new medium, feeding hasn't been aggressive – Runoff EC is low – Single deficiency symptom, nothing else overlapping – Deficiency appeared early in the cycle when soil is still fresh
The diagnostic question to ask yourself: “I'm seeing [symptom]. What have I been feeding heavily that might be blocking this?” If the Mulder's table shows a plausible answer, that's your starting point.
What to Do When You Suspect Antagonism
- Stop adding the blocked nutrient. More iron won't fix iron lockout.
- Identify the likely excess using the table above. What have you been stacking?
- Reduce that input. In DWC, replace the reservoir and mix fresh at lower concentration. In coco, back off feed strength and let runoff EC drop. In soil, a water-only cycle at half strength is usually enough to start clearing it.
- Let runoff EC normalize before resuming full feeding.
- Reintroduce the blocked nutrient at a conservative dose once the excess has cleared.
Don't automatically reach for a full aggressive flush. Antagonism builds gradually and usually unwinds gradually too. You're correcting a balance issue, not nuking the root zone – unless the situation is severe, ease into it.
How PlantLab Applies Mulder's Chart
PlantLab's /diagnose endpoint detects individual nutrient deficiencies from photos. When we built the nutrient subclassifier, the hardest cases weren't single deficiencies – they were patterns where three or four micronutrients were suppressed simultaneously. Those cases almost always had a single excess driving them, not three separate missing nutrients.
So we encoded the Mulder's Chart antagonism graph directly into the analysis layer. Every diagnosis now returns a mulders_hypotheses field: a ranked list of the most likely excess-nutrient candidates, inferred from the co-occurring deficiency pattern.
Here's what that looks like in practice. If the model detects iron deficiency + zinc deficiency + manganese deficiency in the same image:
{
"mulders_hypotheses": [
{
"excess": "phosphorus_excess",
"explains": ["iron_deficiency", "zinc_deficiency", "manganese_deficiency"],
"evidence": 2.38,
"evidence_count": 3
},
{
"excess": "calcium_excess",
"explains": ["iron_deficiency", "zinc_deficiency", "manganese_deficiency"],
"evidence": 2.38,
"evidence_count": 3
},
{
"excess": "zinc_excess",
"explains": ["iron_deficiency", "manganese_deficiency"],
"evidence": 1.61,
"evidence_count": 2
}
]
}
Example reflects multi-label nutrient detection shipping in the next release.
The evidence score is the sum of confidence scores for each condition the excess would explain. Phosphorus and calcium both explain all three deficiencies equally in this example – both rank first. Zinc excess only explains two of the three, so it ranks lower.
This is a hypothesis, not a measurement. The model doesn't have access to your water report, feeding history, or what's in your soil. What it gives you is a starting point: here's which excess is most consistent with the visual pattern. For most growers, that's the hardest part of the diagnosis loop – not knowing which direction to even look.
For growers running API-driven automation – Home Assistant, Node-RED, custom controllers – the mulders_hypotheses field maps directly to an action: phosphorus_excess → reduce P in next feed. The diagnosis points you to the problem; your setup handles the correction.
Limitations
This is inference, not measurement. A soil test or water analysis gives you actual numbers. mulders_hypotheses gives you ranked hypotheses based on what the plant looks like. Use it to direct your investigation, not replace it.
pH is a parallel problem. Deficiency symptoms caused by pH outside the optimal range look identical to antagonism symptoms. If your runoff pH is off, fix that first – the Mulder's table won't help you here.
Rare interactions have less training data. Copper deficiency is a newer addition to the model; detection confidence is lower than for iron or nitrogen. Treat copper-related hypotheses with more skepticism until more data accumulates.
Visual overlap is real. Late-stage symptoms, nitrogen toxicity masking other issues, and grow-stage-specific presentation can confuse any visual analysis. If a diagnosis doesn't match what you're seeing, trust your eyes and reach for a test kit.
Related Reading
- Yellow Leaves, Seven Suspects: How PlantLab Got Specific About Nutrient Deficiencies – how the nutrient sub-classifier powering this was built
- Nitrogen Deficiency in Cannabis – the most common deficiency, and how to tell it apart from light deficiency and senescence
Try PlantLab free at plantlab.ai. Create a free account and get 3 diagnoses per day — upload a photo and the diagnosis returns structured JSON: conditions detected, confidence scores, and the mulders_hypotheses field for any nutrient patterns that fit the antagonism graph.
”You GOT this!”!
from  The happy place
The happy place
I had something on my mind, I couldn’t sleep because I needed to get it out of my system, but I have forgotten what it was.
It has been like this all week; my mind has been wandering to useless places; when I try to focus, I forget on what and then when I remember, and say it’s something on the computer, so that requires 2FA, of course it does, so I pull out my mobile phone, but forget why so instead I watch this clip of ”The Last of the Mohicans” soundtrack, now played on an ancient Celtic instrument.
But it’s only Monday
I dreamt we were having something like sushi for dinner, and there was a giant scampi there, size of a tennis ball, which was jumping around, screaming with this terribly loud shrimp voice, bouncing and hiding in the blue sofa: he wanted so desperately to live, but we had our minds fixed to eat him
It felt terrible, like the way cats sometimes play with ducklings sadistically (it appears) before they eat them
Yes! I remember now, the forgotten thought which triggered a burst of inspiration:
there’s a children’s tooth brush in our bathroom, baby blue plastic with a soccer ball printed on it and the text ”You GOT this!”!
That’s what I was thinking about
In general such motivational texts I think fall flat as they can’t possibly know who they are targeting and to what they refer, but still
I GOT this!
Needs unfilled
from An Open Letter
To be fully honest, the only need that gets left neglected when not in a relationship is sex. Everything else through some extent I can fill through other ways. I also do think that validation is something that I will be missing, and I think maybe it’s a noble goal to pursue feeling like I don’t even need external validation.
I would also like to learn more about the abundance mindset, I’d like to focus more on believing that there are plenty of wonderful women out there that will match my energy, both the chaotic sides, and also the emotionally intelligent sides. I think the more I’ve thought about it, the more I’ve really liked the idea of having a partner that’s similar to me in terms of intelligence. I think there’s so many nice knock on effects from that, like I think humor is a good signal, I think the ability to change is really nice, the ability to do things at a higher level is also really fun, and it reminds me of something my therapist said in a way. My therapist mentioned how someone who has their life together, it is successful and financially independent, how that’s a strong signal that correlates with emotional intelligence. Mostly just because when you have those basic needs met, you have the room to focus on emotional growth, similar to Maslow‘s hierarchy of needs. And also there’s the massive benefit of dual income which would be fucking fire, because I already make a lot of money on my own. I think if my future partner is also successful, having that level of wealth would be fucking awesome. Like I think that level of wealth really enables stuff like traveling the world, or being able to get a lot of really cool luxury things, like PC stuff, nice furniture, and of course the financial freedom. I already have the house part covered, and so I think if I can find a partner that is in a similar financial situation to me, that would be absolutely financial freedom.
China International Leadership Programme Module 1 Overview
from  China Internship
China Internship

China International Leadership Programme Overview
The China International Leadership Programme is a blended China internship programme offering Mandarin immersion, cultural engagement, site visits, and teaching placements in China. This international internship programme combines online modules with immersive, on-the-ground experience in China, giving participants practical exposure to Chinese language, culture, education, and community life. It develops global leadership skills while enabling participants to make a meaningful difference in rural Chinese communities through teaching, service, and cross-cultural engagement.
The China Internship Programme is delivered by the Ireland Sino Institute, which is duly registered in China with both the Ministry of Education and the Ministry of Civil Affairs. It is legally authorised to facilitate Z visa applications for incoming interns. It also maintains registered offices in Ireland and the United Kingdom.
China International Leadership Programme Module 1 Overview (Online)
This module provides applicants with an introductory session and individualised guidance tailored to their specific circumstances. It also includes a formal interview, résumé preparation support, and assistance in securing required documentation, including an apostilled degree, apostilled police clearance, TEFL or TESOL certification, and a professional recommendation letter. The mode of delivery is online.
To register for or to learn more about the China Internship Programme, you can visit AllThingsChina.
2026-03-08
from Two Sentences
Another surprisingly social day chatting with neighbors. The sun shone just long enough for me to run my long run too — what luck.
A New Clearing on the Road
from Wayfarer's Quill
I’ve carried these words across a few landscapes now — small cabins, quiet platforms, places that felt promising but never quite became home.
For now, I’ve set my pack down here on Write.as. I’m curious about this place: its stillness, its simplicity, its promise of a slower web. I’ve brought the older entries with me, the ones written along the road, so the trail behind me is still visible.
I’m not sure yet if this will become the long-term home of Wayfarer’s Quill, but I’m hopeful. I’m here to see what this space offers, how it feels to write within its walls, and whether the quiet here is the kind that invites me to stay.
For now, I’ll linger. And write. And see what unfolds.
#NewBeginnings
Current vibe
from  Talk to Fa
Talk to Fa
Siv's Day
from  Tales Around Blue Blossom
Tales Around Blue Blossom

Abandoned again. Well, not abandoned, but that's what it felt like. Siv brushed down the front of her long bekae, which was a long piece of sky blue cloth she pulled over her head and cinched at the sides with a wide violet sash. It allowed her a lot of movement as it didn't restrict her legs. Yes, her hips showed easily, but she didn't mind. She preferred the freedom of movement. Not only that, she had trained as a smekihanxa with the Peridot Order of House Aldinav. As a courtesan in training, it meant she was used to being around people of higher ranks than most maids and was much more familiar. Siv had learned the art of the laugh, the witty banter, and how to touch someone's arm or shoulder in just the right way to make them relax. Unfortunately, she wasn't cut out for courtesan work after causing a rather embarrassing situation between two houses. Since then it had taken practice to remember how proper she should be.
Siv shivered at that thought but focused on what she was doing now. She was an Estate Maid of the 1st Order and a Mistress Apprentice. Those were big things to focus on, but the young woman had earned Mistress Maevin Maer's trust. Siv had been left in charge as Mistress in Standing since Maevin had to handle the Council of Servants for the planet. That was not something Siv wanted to be involved with.
Smoothing her dress out once more, checking the red silk scarf around her waist and running her hands through her two-tone hair, Siv gently rapped on the wooden door of her Lord's office.
“Come in!”
Henry Patton always sounded so exuberant. His curiosity and fascination always brought a smile to Siv's face. He was even gentle with her and the servants, which endeared everyone to him even more. The young woman stepped in, placed one hand atop the other at her waist, and bowed.
“eta mleteematae Siv kive, xixihanvashav.” Siv is here to serve, my master.
“Oh! Siv!”
There was that smile. Her lord was quite excited today. He had a bunch of compu-pads all over his desk, their crystal screens catching the sunlight through the window at odd angles. The entire desk had the look of someone who had been digging through information for the better part of the morning. The window behind him was wide open and a nice breeze was blowing through.
“I have something for you to do. Maevin was going to handle it but things got moved up; she's on the other side of the planet you know.”
Yeah, she knew. The world of the Houses was always moving and it was a delicate dance due to how much the houses could mistrust each other.
“What is it that you require me to do?”
“It's about the veehanaeset.”
The Soft War. Yhe meeting that Lord Henry was putting together with the estates on the planet. The woman's heart jumped slightly at the word. Yes, of course there were other estates here. Victory was an important hub, though House Avernell was the dominant one. Unlike smaller planets that may only have one estate, this planet meant the dance was much more subtle and intense.
“And how can I help with that?”
“I have been informed that Iron Forge, Black Fall, Morning Dew, and Crystal Spring estates are going to be here later this afternoon. They're sending representatives to hammer out the details among the orders before their lords and ladies arrive.”
Siv swallowed. Now she wished she was at the Council of Servants. What Henry was telling her was that she was going to be responsible for negotiating with rival houses on how the entire event was going to go. By the gods, she wished Maevin were here. When it came to her training, Siv did not have much.
“Do you have a list of those who are coming as representatives?” Siv asked, trying to sound calm and not as nervous as she was.
“Let's see. Mistress Niva Atama of Iron Forge, Steward Vedarat of Black Fall, Lady Halesia of Morning Dew, and Estate Maid of the 1st Order Minaka of Shova.”
A lady. Siv swallowed. Not only were there two servant leaders coming but a Lady, a lady who, if memory served, was the first wife of the Duke of House Nevakev.
“Are you alright?”
Lord Henry's voice cut through the chattering voices in her head. The maid bowed more deeply to hide the embarrassed flush in her face. “I apologize, my master. I was simply caught off guard by the rankings of those coming. I am only a Mistress Apprentice.”
Henry nodded and then set down the compu-pad he had been holding. “Siv.”
The woman looked up to see her master looking right at her.
“While Maevin is gone, you are my mistress. I don't care that your title has 'apprentice' attached. You are to be respected like a mistress, and if they don't, I expect you to tell me. No one is going to be insulted here just because I'm human.”
Siv's heart trilled a bit in her chest at such a vehement defense of a servant. No wonder so many maids had crushes on him.
“As you wish, my master.”
The living room was not really massive, but the way the furniture had been placed gave the area a feeling of grandeur. The sofas had been placed against the walls, with another lush one close to the center. There were a few large, firm cushions for people to lounge on if they preferred to stretch out. Comfort was the spirit of House Avernell.
The hardest thing was waiting. Siv had asked Nish if she would escort the arrivals to the living room. That woman was very steady and level-headed, unlike her lover Abiva. The Mistress Apprentice wanted to be there herself but that would weaken her position. Maevin never went to meet any other servant except when it was a person of high stature. It twisted her gut trying to decide how to treat Lady Halesia, and the Emissary maids were no help. The protocol for the wife of a lord who didn't hold a title except by marriage was a very big gray area. In the end, the young woman had decided to wait here and ask Nish to show far more deference to her than to the others. Hopefully that wouldn't get her into trouble.
When she heard the patter of feet coming, Siv took a deep breath, smoothed down her dress, and turned, trying to smile warmly but in charge. The group of people who came in were jarringly different from each other.
Nish led the way. The woman with the blonde short-cut hair placed one hand on the other in front of her waist and bowed. Siv appreciated the fact that the Arch Maid bowed much further than she needed to, helping cement that Siv was in charge. Behind her came the others.
The first was someone that Siv recognized immediately. They had had enough dealings with Iron Forge Estate that only the newest people did not know Mistress Niva Atama. The woman was the opposite of how the Mistress Apprentice was dressed. A long charcoal black robe trimmed in gold wrapped around her, the rich material catching the natural light as she moved. Her silver hair was in three braids that wound down her head and faded into a dark brown, almost blending with her clothes. A rather ornate gold crown sat on her head, the gems dangling from it bouncing as she walked. A thick dark yellow sash was wrapped around her waist and she wore matching gauntlets of metal that gleamed in the light. For anyone else this would be a weapon and forbidden, but Siv knew she had earned those by fighting off a Drull attack in a different star system. They were her badges of honor, and the Mistress Apprentice had no pressing reason to ask for their removal. The way that Niva watched her, Siv was pretty sure she was waiting for a challenge.
The next to come in was a tall man wearing simple pale blue robes that fit him well and had larger, pointed shoulders, a style common among House Devenek. The silver sash around his waist denoted that he was a Steward, the male equivalent of a Mistress, and this had to be Vedarat. The man gave her a nod of acknowledgement.
The last two came in together, one all gentle smiles and the other quiet.
“xikihanma daexugee!” Lady Halesia said, reaching out with both hands, striding forward, and taking Siv's in her own. “It is so wonderful to meet you. I have heard of you and your training under Mistress Maer. It is sad that she is not here for me to compliment your skills.”
Siv did her best not to blush. A Lady of another house complimenting her?
Halesia carried herself with an effortless grace that drew the eye immediately. Long, wavy hair cascaded past her shoulders, pinned back with a delicate bow that softened the sharp elegance of her features. Her face was warm and open, lips curved into a smile that suggested she knew exactly the effect she had on people and probably enjoyed it.
Her outfit hugged her figure closely, a fitted bodice cinched at the waist, paired with sleek dark leggings that disappeared into tall boots. When Halesia spoke, her voice carried a practiced charm, her words chosen with ease. She had made no visible effort to do anything except greet them, but Siv already felt that she could easily take over the discussion. So many powerful figures here and she was on her own.
Don't screw this up, the Mistress Apprentice scolded herself.
The last person was Estate Maid of the 1st Order Minaka of House Shova, and it took everything in her not to startle. Large, jagged white scars ran down the left side of her face, marring her look. Her dark eye on one side moved while the other was a white electronic eye with electric blue veins. This woman had been through something. The sitting room felt smaller with all of them in it.
Siv gestured to the sofas and cushions, keeping her expression warm and her voice as even as she could pull off. “Please, make yourselves comfortable. Refreshments will be brought shortly.” She had already arranged for Burdak to have a few of his maids bring tea and the eflen cakes that were a specialty of House Avernell's kitchens.
Niva did not so much sit as install herself. She chose the central sofa, spreading the weight of her charcoal robes around her like a declaration of territory and placed her gauntleted hands on her knees. The gems on her crown caught the afternoon light coming through the wide window and threw small bright shapes across the ceiling.
Vedarat settled into the armchair to the left, crossing one leg over the other and folding his hands in his lap. He said nothing yet, but his eyes moved around the room with a slow, measured attention that reminded Siv of someone taking inventory. Hadn't Maevin said the quiet ones should be watched the most?
Lady Halesia settled gracefully onto one of the firm cushions near the center, tucking her legs neatly beneath her and smiling as though this were a pleasant social call rather than a negotiation. Minaka positioned herself slightly behind and to the right of Halesia, spine straight, scarred face unreadable, her mismatched eyes fixed on the middle distance. Siv took her place standing before them, hands folded at her waist.
“I want to thank each of you for coming on behalf of your houses. Lord Henry is honored by the presence of such distinguished representatives and wishes this meeting to be fruitful for all parties.” She paused just a breath. “I also want to acknowledge that Mistress Maer would normally be conducting these discussions. In her absence, Lord Henry has placed his full confidence in me, and I intend to honor that trust.”
She watched Niva's expression during that last part. The Mistress of Iron Forge did not roll her eyes exactly. She simply let her gaze drift to the window and back in a way that communicated everything without committing to anything.
“As your presence is a tentative agreement to participate in the veehaneaset, it is important for us to make sure that everyone is comfortable. This is supposed to be an informal gathering and my master has made it clear he wants comfort and safety to outweigh any ceremony.” Siv said, trying not to let the words all spill out.
“Outweigh ceremony?” Niva's voice was smooth and low and carried the particular weight of someone who had never been told no and had survived it. “That is a very generous sentiment.”
“Blue Blossom Estate extends it sincerely.”
“Then perhaps your master can explain how this can be maintained when tradition is important not only to my house but to others like House Shova?” Niva leaned forward slightly, the dangling gems of her crown swaying. “Tradition has been a part of our culture as long as we can remember and cannot be thrown aside at the whims of a Terran. This is fact.”
“If I may,” Halesia said, her voice slipping into the conversation like warm water finding a gap between stones. She smiled at Niva with what looked like genuine friendliness. “House Patton-Avernell holds a charter from the Empress herself. It stands to reason that this house's preference of minimal ceremony is their specific culture. It would not look good upon any of our estates if we simply dismissed their approach.”
Niva's jaw shifted slightly. She sat back.
Siv exhaled through her nose. The verbal fencing had already begun and it took everything not to tremble from the adrenaline running through the Mistress Apprentice's system.
“My master wants the representatives to feel as safe and welcome as possible,” Siv continued, drawing their attention back. “He wants genuine conversation without the trappings of prestige, for the betterment of all estates here on Victory.”
“I have heard Lord Patton-Avernell's own words offering support to my estate,” Vedarat's voice was calm and matter-of-fact. He had not changed his posture at all.
“Words are worth only the sound they make,” Niva responded with a curl of her lip.
Steward Vedarat slowly turned to look at the other peer, holding her gaze. “Which he has carried out. His lord has submitted official paperwork to authorize House Devenek's participation in the Starbase upgrades.”
Niva's eyes narrowed, something calculating behind them, but she did not say anything more. The room was quiet for a moment.
Siv glanced briefly at Minaka, who had not moved, had not spoken, and appeared to be semi-focused on something outside the window rather than the meeting going on. There was nothing hostile in it, almost as if this conversation was not interesting to her.
Siv straightened slightly and moved to the next point.
“The ancient tradition of veehaneaset carries an expectation of gifts to begin the event, something that our Emissary maids made clear to my master could not be dispensed with.” There were some things that simply could not be dispensed with.
Niva's chin lifted.
Here we go, Siv thought.
“Iron Forge intends to defer such discussions at the moment.”
Everyone shifted uncomfortably. It took everything for the Mistress Apprentice not to say something. Niva was really pushing the boundary of what she would be allowed to get away with.
Siv kept her voice even. “Still, such things must be planned for, as allowing the insult of any estate or house is something my master will not permit.”
“My husband has prepared a donation of currency toward the upgrades of the starbase we were speaking of earlier,” Halesia said lightly, “to help defray the pressure that would put on House Patton-Avernell.”
Niva frowned and Vedarat straightened.
“Such a substantial gift for a project that one is not part of is...interesting,” Vedarat said with narrowed eyes.
“Peace, Steward,” Halesia said with a mischievous smile. “We donate it in the spirit of the veehaneaset with no expectation except as proof of House Nevakev's trust in Lord Patton-Avernell's leadership.”
The Mistress Apprentice wasn't sure if that helped or not. The politics was choking. How did Maevin handle all of this?
For the next two hours they pressed on with discussions of lodging, how many security personnel, what was expected of any honored maids, down to the mundane of how meals would be prepared and so forth. Even so, in the back of Siv's mind, she knew Minaka had not said anything, had not engaged in a single discussion point.
As they were wrapping up, the 1st Order Maid stood, drawing everyone's attention.
“Crystal Spring Estate of House Shova will not be participating in the veehaneaset.”
Her voice was low and even and carried no apology in it whatsoever. Minaka didn't bother to look at anyone but turned on her heel and left through the door she had come in. The silence she left behind lasted exactly two seconds.
“Well,” Niva's voice cut across the room like a blade finding a seam. “That is rather expected of House Shova, isn't it. They refuse to participate in anything that could put their precious knowledge at risk, even if it means insulting the ruling estate.”
Halesia's smile had gone carefully neutral. Vedarat had gone very still in the particular way of someone who was deciding whether this was his problem. Siv's heart was hammering. She could feel it at the base of her throat. Siv did not let herself swallow visibly. She kept her hands folded at her waist and her expression warm and in charge, completely at odds with the cold spiral happening behind her eyes.
“Please forgive the interruption,” she said, and was relieved to hear her own voice come out steady. “I wonder if I might impose on your patience a little longer. I believe Nish was preparing a second round of refreshments.”
As if summoned by the words themselves, Nish appeared in the doorway with a tray of small glazed pastries and a fresh pot of something that smelled of spice. The Arch Maid moved through the room with her particular brand of unhurried competence, setting the tray down and meeting Siv's eyes for only a fraction of a second.
The nod was so small it was barely a movement at all.
She heard Halesia begin to say something gracious to Nish as the door closed behind her.
The corridor outside was empty and cool, and Siv allowed herself exactly four fast steps of genuine panic before she locked it back down and broke into a purposeful stride toward the estate's front approach.
Minaka had not been hurrying. Siv caught sight of her just as the woman turned the far corner of the main corridor that led toward the outer courtyard and the shuttle landing pad beyond it. Her pace was measured; she moved like someone who had already finished a task and was simply in the process of leaving it behind.
“Peer Minaka,” Siv said, referencing that she was also a 1st Order Maid when not a Mistress Apprentice.
The woman stopped but did not turn immediately. There was a pause, brief but present, and then she turned on her heel and faced Siv with that still, unreadable expression.
Siv stopped a few paces away and kept her voice level.
“I would ask a few minutes of your time.”
Another pause. Then Minaka inclined her head. Not warmly. But she inclined it.
Siv chose her words with the same care she would choose footing on uncertain ground. “May I understand why you have refused my master's invitation? Did I not convey to you his sincerity, of safety, with no design upon you or the others?”
For a moment she thought Minaka might not answer, but she spoke. “He may speak of no design, but how can a human be trusted? Let alone any of those in that room. My estate and house are of history and of secrets. Every house has tried to vie for our favor or coerce us into obedience, to use what we know for their own gain. Why would this be any different?”
She said it without heat. That was somehow the most unsettling part.
“Lord Henry is not like that,” Siv said.
Minaka's expression shifted into something like amusement. “A Terran? Really? I would not have expected you to be so naive, Peer Siv.”
Siv stood very still for a moment. Then she made a decision. It was probably reckless. Maevin would have thought carefully about it for at least ten minutes before committing. Siv gave herself three seconds and moved.
“Come with me,” she said.
The southern garden was not the estate's most impressive space. That distinction belonged to the formal courtyard near the entrance with its sculpted hedges and fountain that caught the light at dawn in a way that made visitors stop walking. The southern garden was where things actually grew, vegetable beds, herb rows, the stubborn sprawling tangle of something that Burdak had been cultivating and refused to explain. It smelled of turned earth and something green and faintly sweet, and the evening light came through the trees at the garden's edge in long, low bars of amber.
Siv slowed as they approached the garden wall and held out a hand, briefly, to stop Minaka beside her. She positioned them at the corner where the wall's shadow was deep and the sightline through the garden gate was clear.
Lord Henry was on his knees in the third vegetable bed.
He had what appeared to be dirt on both forearms up to the elbow and was pulling weeds from the base of a row of something leafy with the focused enthusiasm of a man who had absolutely no intention of returning to his paperwork. Two maids worked nearby, one on each side of him, and the sound of their voices drifted across the garden in the evening air.
He was laughing. Something one of the maids had said had caught him entirely off guard and he had sat back on his heels and laughed with his whole face, with no performance in it whatsoever.
The maid was grinning, far too comfortable for someone working with a lord of an estate, but that was the point Siv was trying to make.
Henry said something back. Siv couldn't catch the words but she watched the maid laugh again. Henry went back to his weeding. He did not look up toward the wall. He had no idea anyone was watching.
Siv looked at Minaka. The woman was very still. Her scarred face was turned toward the garden and her expression had changed in some way that was difficult to name. The electronic eye moved, tracking slowly across the scene. The dark eye beside it had something in it that it hadn't had before. The silence stretched out between them, easy now in a way it had not been in the corridor.
After a long moment, Minaka exhaled through her nose. It was a small sound. Almost nothing.
“He has no idea anyone is watching him,” Minaka said quietly. It was not quite a question.
“No.”
Minaka was quiet for a long time. Down in the garden, Henry said something that made the maid cover her mouth with her dirt-covered hand, though she quickly composed herself, while Henry looked very pleased with himself.
Minaka watched this. She watched all of it.
Then she said, without looking away from the garden, “This one time.”
Siv turned her head.
“House Shova,” Minaka said, “will send a representative.”
She said it the way she had said everything else today, flat and even and without decoration. The weight on Siv's shoulders lifted and she almost took in a ragged breath.
“Thank you,” Siv said. She kept her voice just as quiet.
Minaka turned from the garden and straightened her shoulders. The scarred face was composed again, the moment tucked away somewhere Siv could not follow it.
“I will see myself to the landing pad,” she said.
Siv nodded and watched her go.
There was definitely a look of disbelief on everyone's face, especially Niva's, when Siv returned to inform them that House Shova would be participating. She did not go into detail, as it was time for everyone to leave.
The moon was shining bright as Siv looked over the belvedere wall, noting the maids returning in from their shift. She also noticed Abiva swatting the backside of a certain yellow-haired maid who had probably screwed up something yet again.
“I am impressed.”
Siv nearly came out of her skin at the cool voice beside her. Siv turned with a start to see Mistress Maevin standing there, looking out toward the woods in the distance.
“xikihanmaav,” Siv said with a quick bow. “I did not see you there.”
Maevin raised a hand to ward off the politeness and turned to look at the other girl. “House Shova has never accepted invitations. They have always sent a representative but never followed through.”
There was a glitter of curiosity in Maevin's eyes. “I would not have been confident that even I could have gotten them to agree. What did you do?”
Siv thought about it. Yes, she had gambled and it had paid off, but she had also exposed her master's private life in a way that could have been used against him. Siv would either be rewarded or tied to the pillar. So she lowered her head.
“You once told me that we must learn how to navigate things ourselves and to find ways of getting things done,” Siv said.
“Yes?”
“I have found a way.”
“You don't plan on telling me,” Maevin said with a hint of amusement and irritation.
“What sort of mistress would I be if I gave away my secrets?”
That did get a chuckle out of the imperious woman who ruled the estate with an iron fist.
“Go to bed, Siv. You've earned it.”
Yes. She had.
More Tools Made AI Worse: The Engineering Fix Now Reshaping Agentic Systems
from  SmarterArticles
SmarterArticles

Something strange happened in late 2025. Engineers at Anthropic noticed that their AI agents were choking on their own capabilities. The more tools they connected, the worse their systems performed. A typical setup linking five common enterprise services (GitHub, Slack, Sentry, Grafana, and Splunk) consumed roughly 55,000 tokens just in tool definitions before the agent had even read a single user request. One internal deployment devoured 134,000 tokens on tool descriptions alone, leaving the model precious little room for actual reasoning. It was the software equivalent of filling a filing cabinet with instruction manuals and leaving no space for the files themselves.
The irony was exquisite. The Model Context Protocol, Anthropic's open standard for connecting AI agents to external systems, had succeeded beyond anyone's expectations. Launched in November 2024, MCP had grown from an internal experiment into the dominant integration standard for agentic AI, with over 10,000 active public MCP servers by late 2025 and adoption by ChatGPT, Cursor, Gemini, Microsoft Copilot, and Visual Studio Code. Official SDK downloads exceeded 97 million per month across Python and TypeScript. But this success created a paradox: the more tools agents could access, the less effective they became at using any of them.
The team's response, detailed in Anthropic's engineering blog post on advanced tool use, was not to limit tool access but to fundamentally rethink how agents discover and interact with their capabilities. The result was a trio of features that, working together, reduced context consumption by up to 85 per cent while simultaneously improving accuracy. And the design patterns they established are now reshaping how the entire industry thinks about building production agentic systems.
When Every Tool Costs You Tokens
To understand why the tool scaling problem became acute in 2025, you need to appreciate the economics of context windows. Every tool definition an agent loads carries a token cost. A modestly complex tool with a name, description, and parameter schema might consume 200 tokens. That seems trivial until you connect to a GitHub MCP server with 35 tools (roughly 26,000 tokens), a Slack server with 11 tools (21,000 tokens), and a handful of monitoring services. Suddenly, you have burned through tens of thousands of tokens before the conversation even begins.
Bin Wu, the primary author of Anthropic's advanced tool use engineering blog post and a former Airbnb engineer who joined Anthropic to work on AI safety, described the problem in stark terms. The traditional approach to tool management, loading all definitions upfront and passing them to the model, simply does not scale when developers are connecting agents to dozens or hundreds of MCP servers. Anthropic's internal testing revealed that tool selection accuracy degrades significantly once you exceed 30 to 50 available tools. The model gets overwhelmed by options, like a diner handed a 200-page menu when they just want breakfast.
This degradation is not merely anecdotal. Research on large language model tool calling has consistently demonstrated a negative correlation between tool library size and selection accuracy. The phenomenon has multiple causes. Context window saturation leaves less room for reasoning as tool definitions consume more space. The well-documented “lost in the middle” effect means models recall information at the beginning and end of their context windows more reliably than content buried in the middle, causing optimal tools to be overlooked when they appear amidst dozens of alternatives. And larger context windows alone do not solve the problem, because the core attention and selection accuracy issues persist regardless of how much space is available.
This problem has two distinct dimensions. The first is what engineers call “context bloat”: tool definitions consuming the finite token budget that the model needs for reasoning, user instructions, and conversation history. The second is “context pollution”: intermediate results from tool calls flooding the context window with data the model does not actually need. A two-hour sales meeting transcript routed through a workflow might mean processing an additional 50,000 tokens of audio transcription, even when the agent only needs a three-sentence summary.
As Adam Jones and Conor Kelly detailed in Anthropic's companion post on code execution with MCP, these two inefficiencies compound each other in production environments. An agent connected to thousands of tools must process hundreds of thousands of tokens in definitions before it even reads the user's request, and then each tool invocation potentially dumps thousands more tokens of intermediate results back into the context window. The practical ceiling is not the model's intelligence. It is the model's context budget.
The financial implications are equally pressing. Token usage translates directly into API costs. An enterprise running thousands of agent interactions daily can see its compute bills balloon when every request begins with 100,000 tokens of overhead. Latency suffers too: more input tokens mean longer processing times, which means slower responses, which means frustrated users and abandoned workflows. Before MCP, developers faced what Anthropic described as an “N by M” integration problem: ten AI applications and one hundred tools could require up to a thousand different integrations. MCP solved that problem elegantly, reducing it to a single protocol implementation on each side. But it introduced a new one: the protocol worked so well that developers connected everything, and the resulting token cost became unsustainable.
The Discovery Revolution
Anthropic's first intervention was the Tool Search Tool, a meta-capability that lets agents discover tools on demand rather than loading everything upfront. The concept is deceptively simple. Instead of passing all tool definitions to the model at the start of every conversation, developers mark tools with a defer_loading: true parameter. These deferred tools are not loaded into the model's context initially. The agent sees only the Tool Search Tool itself, plus a small set of frequently used tools that remain always-loaded. When the agent encounters a task requiring a specific capability, it searches for relevant tools, loads only the three to five it actually needs, and proceeds.
The token savings are dramatic. That five-server scenario consuming 55,000 tokens in definitions? With the Tool Search Tool, it drops to roughly 8,700 tokens, preserving 95 per cent of the context window. Across implementations, Anthropic documented an 85 per cent reduction in token usage while maintaining access to the full tool library. The system supports catalogues of up to 10,000 tools, returning three to five of the most relevant per search query.
But the real surprise was accuracy. Conventional wisdom suggested that reducing the number of visible tools would degrade performance, forcing the model to take an extra step to find what it needs. The opposite turned out to be true. By surfacing a focused set of relevant tools on demand, tool search actually improved selection accuracy, particularly with large tool libraries. Internal testing on MCP evaluation benchmarks showed Claude Opus 4 jumping from 49 per cent to 74 per cent accuracy, a 25 percentage-point improvement. Claude Opus 4.5 improved from 79.5 per cent to 88.1 per cent. The mechanism was straightforward: fewer options meant less confusion, and dynamically selected tools were more likely to be relevant to the actual task.
The Tool Search Tool supports multiple search strategies, each suited to different deployment needs. The regex-based variant, designated tool_search_tool_regex_20251119, uses Python's re.search() syntax and works well for keyword matching across tool names and descriptions. It supports exact matches, flexible patterns using wildcards, and case-insensitive searches with a maximum query length of 200 characters. The BM25-based variant, tool_search_tool_bm25_20251119, accepts natural language queries instead, using term-frequency ranking for more nuanced discovery. Both variants search tool names, descriptions, argument names, and argument descriptions. Custom embedding-based search offers a third option, enabling semantic matching that finds tools by meaning rather than exact terminology. Developers can implement whichever strategy suits their deployment, or combine them.
There is also a caching advantage that was not immediately obvious. Because deferred tools are not included in the initial prompt, the rest of the prompt remains stable across requests. This makes prompt caching significantly more effective, since the cacheable portion of the prompt does not change every time the tool set shifts. For high-volume deployments, this secondary optimisation can compound the primary token savings substantially.
Cloudflare arrived at a strikingly similar conclusion through independent research, publishing their findings under the banner of “Code Mode” in September 2025, roughly two months before Anthropic's November announcement. As Cloudflare's engineering team observed, with just two tools, search() and execute(), their server could provide access to the entire Cloudflare API over MCP while consuming only around 1,000 tokens. When new products were added, the same search and execute code paths discovered and called them automatically, with no new tool definitions and no new MCP servers required. The generated JavaScript runs in a secure, isolated V8 Worker sandbox with external network access blocked by default, and each execution receives its own Worker instance.
The convergence was striking. Two major technology companies, working independently, identified the same fundamental problem and arrived at architecturally similar solutions within weeks of each other, as noted in the Cloudflare Code Mode blog post. Cloudflare published on 26 September 2025; Anthropic followed on 4 November 2025. The posts reference each other, but these were clearly parallel discoveries driven by the same pressures: agents were scaling up, tool counts were exploding, and the old approach broke at this scale.
Writing Code Instead of Making Calls
The second major innovation was Programmatic Tool Calling, which addresses the context pollution problem rather than context bloat. Traditional tool calling works through a sequential loop: the agent requests a tool, the API returns the result, the result enters the model's context, and the agent decides what to do next. For simple workflows involving two or three tools, this is fine. For complex orchestration spanning 20 or more tool invocations, it becomes catastrophically expensive.
Consider a practical scenario: checking budget compliance across 20 team members. In the traditional approach, the agent calls a tool to retrieve each team member's spending, waits for the result, processes it in context, and calls the next tool. That is 20 round trips through the model, 20 sets of intermediate results flooding the context window, and 19 additional inference passes that each add latency and cost. Anthropic measured one such workflow consuming 43,588 tokens across all those sequential invocations.
Programmatic Tool Calling flips this model. Instead of requesting tools one at a time, the agent writes a Python script that orchestrates the entire workflow. The script runs in a sandboxed Code Execution environment, pausing when it needs results from external tools. When tool results return via the API, they are processed by the script rather than consumed by the model. The script handles loops, conditionals, error handling, and data filtering, and only the final aggregated output reaches the model's context window. In Anthropic's budget compliance example, the same workflow dropped from 43,588 to 27,297 tokens, a 37 per cent reduction on that single task. But the savings compound dramatically with complexity: one implementation documented by Adam Jones and Conor Kelly reduced token usage from 150,000 tokens to 2,000, a 98.7 per cent reduction.
The insight beneath this approach has a certain elegance. Large language models have been trained on billions of lines of real code. They are fluent in Python, JavaScript, and TypeScript. But JSON tool-calling schemas are synthetic constructs that barely appear in training data. Asking a model to orchestrate complex workflows through individual JSON function calls is like asking a concert pianist to play a symphony by pressing one key at a time and waiting for approval between each note. Programmatic Tool Calling lets the model compose the entire piece. Cloudflare's engineering team articulated the same observation independently: models are fluent in real programming languages but stutter when asked to produce function-call JSON, because they have seen millions of lines of actual code during training but only contrived tool-calling examples.
This idea did not appear in a vacuum. Joel Pobar's LLMVM project had been exploring code-based tool orchestration since before it was fashionable, allowing language models to interleave natural language and code rather than relying on traditional tool calling APIs. The project's design philosophy, that letting models write code generally results in significantly better task deconstruction and execution, prefigured the approach that both Anthropic and Cloudflare would later formalise. LLMVM uses a “continuation passing style” execution model, where queries result in natural language interleaved with code rather than a rigid sequence of code generation followed by natural language interpretation.
Anthropic's implementation requires tools to opt in to programmatic calling through an allowed_callers parameter, specifically allowed_callers: ["code_execution_20250825"]. This ensures that sensitive operations can be restricted to direct model invocation with user approval. The sandboxed execution environment provides resource limits and monitoring. Intermediate results stay within the execution environment by default, which also carries privacy benefits: the MCP client can tokenise personally identifiable information automatically, allowing real data to flow between systems while preventing the model from accessing raw PII.
On 17 February 2026, Anthropic moved Programmatic Tool Calling to general availability with the release of Claude Sonnet 4.6, signalling that the feature had graduated from experimental curiosity to production-ready infrastructure. Alongside this, web search and fetch tools gained automatic code-based filtering, cutting input tokens by 24 per cent while boosting BrowserComp accuracy from 33 per cent to 46 per cent. Joe Binder, VP of Product at GitHub, noted that Claude Sonnet 4.6 was “already excelling at complex code fixes, especially when searching across large codebases is essential.” The broader community followed suit: Block's Goose Agent added “code mode” MCP support, LiteLLM added native support across providers, and multiple open-source projects adopted the pattern.
Teaching By Example
The third feature in Anthropic's advanced tool use suite is Tool Use Examples, which addresses a subtler problem than context bloat or pollution: parameter specification errors. Even when an agent correctly identifies the right tool and calls it efficiently, it can still fail by passing malformed or incorrect parameters. JSON Schema definitions tell the model what parameters are available and their types, but they do not convey the conventions, correlations, and formatting expectations that distinguish a correct invocation from a technically valid but functionally broken one.
Consider a calendar scheduling API that accepts a date parameter. The schema specifies that the parameter is a string, but does it expect “2025-11-15”, “15/11/2025”, “November 15, 2025”, or “15 Nov 2025”? The schema might even specify a pattern, but more complex relationships between parameters, such as an “enddate” that must be after “startdate” or a “timezone” parameter that changes the interpretation of datetime values, remain invisible in the formal specification.
Tool Use Examples solve this by providing concrete usage patterns alongside schema definitions. Developers include an input_examples array with one to five examples demonstrating proper parameter formatting and usage patterns. These examples can show minimal parameter usage (just the required fields), partial parameter combinations (common optional parameter groupings), and full parameter specifications (every available option), giving the model a practical understanding of how the tool should actually be called. Anthropic recommends between one and five examples per tool, with each example addressing a different usage pattern.
The impact on accuracy is substantial. Anthropic's internal testing showed accuracy on complex parameter handling improving from 72 per cent to 90 per cent with the addition of Tool Use Examples. As the Setec Research analysis of these features noted, the improvement is particularly pronounced for APIs with ambiguous parameter relationships, where the schema alone does not capture the implicit rules governing which parameter combinations are valid. The feature addresses format conventions that JSON Schema cannot express, nested structure patterns that require demonstration rather than description, and the implicit correlations between optional parameters that experienced developers understand intuitively but struggle to formalise.
This is not a novel pedagogical insight. It is the same principle that makes code documentation more useful when it includes examples alongside API reference descriptions. Developers have long understood that showing is more effective than telling. Tool Use Examples apply this principle to the model-tool interface, giving the agent worked examples rather than abstract specifications.
The three features are designed to work together as a complementary system. Tool Search Tool reduces upfront context consumption by loading tools on demand. Programmatic Tool Calling reduces runtime context pollution by keeping intermediate results out of the model's context. Tool Use Examples reduce errors by teaching the model how to use tools correctly through demonstration rather than description alone. Together, they address the full lifecycle of what Anthropic calls “context pollution in MCP-connected agents,” as described in their advanced tool use documentation.
Scaling MCP Without Breaking the Bank
The practical challenge for enterprises is not adopting any single optimisation technique. It is managing the operational complexity of hundreds or thousands of MCP-connected tools while maintaining the progressive disclosure principles that keep agents efficient. This requires architectural thinking beyond individual feature adoption.
The recommended pattern follows what might be called layered tool management. At the first layer, a small set of three to five frequently used tools remains always-loaded with defer_loading: false. These are the tools the agent will need in nearly every interaction: perhaps a file search tool, a messaging tool, and a general-purpose retrieval tool. At the second layer, entire MCP servers can be deferred with a default_config that sets defer_loading: true across all their tools, with selective exceptions for high-use capabilities within those servers. The example Anthropic provides is a Google Drive MCP server where all tools are deferred except search_files, which remains loaded because it is the most commonly needed entry point.
This progressive disclosure architecture mirrors a principle well-established in user interface design: show users what they need now, and make everything else discoverable. The difference is that here, the “user” is an AI agent, and the cost of poor disclosure is not confusion but wasted tokens and degraded performance.
For organisations operating at genuine scale, with dozens of MCP servers and hundreds of tools, the filesystem-based discovery pattern described in Anthropic's code execution with MCP post offers an alternative architecture. Rather than registering every tool with the API upfront, tools are presented as code files on a filesystem, organised into directories by server. A TypeScript file tree might include paths like servers/google-drive/getDocument.ts and servers/salesforce/updateRecord.ts. The agent explores the filesystem to find relevant tool definitions, reading them on demand. A search_tools utility allows the agent to query for relevant definitions with configurable detail levels: name only, name plus description, or full schemas with parameters. This approach scales elegantly because adding new tools means adding new files, not modifying configuration or redeploying infrastructure.
The governance dimension is equally important. In December 2025, Anthropic donated MCP to the Agentic AI Foundation, a directed fund under the Linux Foundation co-founded by Anthropic, Block, and OpenAI with support from Google, Microsoft, Amazon Web Services, Cloudflare, and Bloomberg. Mike Krieger, Chief Product Officer at Anthropic, explained that MCP had started as an internal project and had become “the industry standard for connecting AI systems to data and tools.” The donation was designed to ensure the protocol “stays open, neutral, and community-driven as it becomes critical infrastructure for AI.” Jim Zemlin, executive director of the Linux Foundation, framed the goal as avoiding a future of “closed wall” proprietary stacks where tool connections, agent behaviour, and orchestration are locked behind a handful of platforms. Platinum members of the new foundation include Amazon, Anthropic, Block, Bloomberg, Cloudflare, Google, Microsoft, and OpenAI, with Gold members including Cisco, Datadog, Docker, IBM, JetBrains, and Oracle among others. This institutional backing means enterprises can invest in MCP-based architectures with reasonable confidence in the standard's longevity and neutrality.
Measuring What Matters
Building efficient agentic systems is one problem. Knowing whether they actually work is another entirely. The evaluation methodologies for tool-using agents are still maturing, but several frameworks have emerged from both Anthropic's internal testing and broader industry practice.
The first and most obvious metric is token efficiency: how many tokens does the agent consume per task, and how does this change as the tool library grows? Anthropic's benchmarks provide useful baselines. A five-server MCP deployment consuming 55,000 tokens in definitions with traditional loading should drop to roughly 8,700 tokens with Tool Search, a reduction that should hold proportionally as the tool count increases. Programmatic Tool Calling should yield additional reductions of 37 per cent or more on multi-step workflows, with higher savings on more complex orchestrations.
But token efficiency alone is insufficient. The more meaningful measure is task accuracy, specifically the rate at which agents select the correct tool, invoke it with proper parameters, and produce the intended outcome. Anthropic's MCP evaluation benchmarks provide one framework for this, measuring tool selection accuracy across varying library sizes. The jumps from 49 to 74 per cent (Opus 4) and from 79.5 to 88.1 per cent (Opus 4.5) with Tool Search enabled demonstrate that efficiency and accuracy can improve simultaneously, rather than trading off against each other.
For Programmatic Tool Calling, Anthropic measured knowledge retrieval accuracy improving from 25.6 per cent to 28.5 per cent, and GIA (General Instruction Adherence) benchmarks rising from 46.5 per cent to 51.2 per cent. These gains are more modest than the tool selection improvements, reflecting the fact that code-based orchestration primarily addresses efficiency rather than capability. But in production systems, small accuracy improvements compound across thousands of daily interactions.
A rigorous evaluation framework should track at least four dimensions. First, context efficiency: tokens consumed per task, broken down by tool definitions, intermediate results, and model reasoning. Second, tool selection precision: the rate at which the agent identifies the correct tool for a given subtask, measured against a labelled test set of tasks and expected tool selections. Third, parameter accuracy: the rate at which tool invocations include correct, complete, and properly formatted parameters. And fourth, end-to-end task completion: whether the overall workflow produces the correct final output, regardless of intermediate steps.
The bottleneck identification process follows naturally from these metrics. If context efficiency is poor but tool selection is accurate, the problem is in loading strategy, and Tool Search is the appropriate intervention. If tool selection degrades with library size, the search implementation needs refinement, perhaps moving from regex-based to embedding-based retrieval. If parameter errors dominate, Tool Use Examples should be expanded. If end-to-end completion lags despite good individual metrics, the orchestration logic, whether sequential or programmatic, likely needs restructuring.
Latency deserves its own evaluation track. Programmatic Tool Calling eliminates the multiple round trips inherent in sequential tool invocation, which should reduce end-to-end latency for complex workflows. But it introduces the overhead of code execution environments. Measuring wall-clock time per task, alongside token counts, reveals whether the computational overhead of sandboxed execution outweighs the savings from fewer inference passes. In Anthropic's testing, a workflow requiring 19 or more sequential inference passes collapsed into a single programmatic execution, a latency reduction that far exceeded any overhead from the sandbox.
Researchers have also proposed broader reliability frameworks for evaluating agentic systems. A 2025 study outlined twelve concrete metrics decomposing agent reliability along four key dimensions: consistency, robustness, predictability, and safety. The findings were sobering. Evaluating 14 agentic models across two complementary benchmarks, the researchers found that recent capability gains had yielded only small improvements in reliability, suggesting that making agents more capable does not automatically make them more dependable. This gap between capability and reliability underscores the importance of dedicated evaluation infrastructure that measures not just whether agents can do things, but whether they do them consistently and safely.
Design Patterns for the Production Frontier
The engineering patterns emerging from these developments suggest a maturation of agentic system architecture. Several design principles have crystallised from both Anthropic's work and the broader community's experience.
The first is what Anthropic calls the “layered approach”: address the highest bottleneck first. If tool definitions consume most of your token budget, start with Tool Search. If intermediate results dominate, implement Programmatic Tool Calling. If parameter errors cause most failures, add Tool Use Examples. This triage prevents premature optimisation and ensures that engineering effort targets the actual constraint.
The second pattern is parallel execution through code orchestration. When multiple tool calls are independent, they should execute concurrently rather than sequentially. Anthropic's documentation references asyncio.gather() for independent operations within programmatic tool calls. This pattern does not reduce token consumption, but it dramatically reduces latency for workflows involving multiple independent data retrievals.
The third pattern involves explicit return format documentation. When tools are called programmatically, the agent's code needs to parse tool outputs reliably. Anthropic recommends explicitly specifying tool output structures in tool descriptions, so the code the model writes can accurately reference fields and formats in the returned data. Without this, the model may generate code that assumes incorrect output structures, leading to runtime failures in the sandbox.
The fourth pattern addresses security and privacy boundaries. Programmatic Tool Calling introduces a new trust surface: the agent is now writing and executing code, not just making predefined function calls. The allowed_callers parameter provides opt-in control, ensuring that sensitive tools (those that modify data, access credentials, or perform irreversible actions) can be restricted to direct model invocation with explicit user approval. Cloudflare's approach adds another layer: bindings that provide pre-authorised client interfaces, ensuring that AI-generated code cannot possibly leak API keys because the keys never enter the execution environment. The binding provides an already-authorised client interface to the MCP server, and all calls made on it pass through the agent supervisor first, which holds the access tokens and injects them into outbound requests.
The fifth pattern concerns state persistence across operations. As described in Anthropic's MCP code execution documentation, agents can maintain filesystem state across operations, enabling resumption of interrupted workflows and the development of reusable functions as “skills” that persist between sessions. This transforms agents from stateless request processors into stateful systems capable of learning and adaptation within their operational context.
For enterprises evaluating these patterns, the critical implementation question is infrastructure. Code execution demands secure execution environments with appropriate sandboxing, resource limits, and monitoring. These add operational overhead compared to direct tool calls. Anthropic's managed implementation handles container management, code execution, and secure tool invocation communication, but organisations with strict data residency or compliance requirements may need to build or adapt their own execution environments. Cloudflare's approach, using Durable Objects as stateful micro-servers with their own SQL databases and WebSocket connections, offers one model for self-hosted execution, deploying once and scaling across a global network to tens of millions of instances.
The broader trajectory is unmistakable. The agent ecosystem is moving away from the “give the model everything and let it figure it out” approach that characterised early tool-using agents. In its place, a more disciplined architecture is emerging: one that treats context as a scarce resource, applies progressive disclosure to manage complexity, and uses code execution to keep intermediate processing out of the model's reasoning space. This is not merely an efficiency optimisation. It is a fundamental shift in how we think about the boundary between what the model does and what the surrounding system does.
As the MCP ecosystem continues to expand under the governance of the Agentic AI Foundation, and as tool counts scale from hundreds to thousands, the organisations that thrive will be those that master this boundary. They will build agents that know how to find the right tool without seeing every tool, that orchestrate complex workflows through code rather than conversation, and that learn from examples rather than struggling with abstract schemas. The 85 per cent context reduction is not the end state. It is the beginning of an entirely new way of building intelligent systems.
References and Sources
Wu, Bin. “Introducing Advanced Tool Use on the Claude Developer Platform.” Anthropic Engineering Blog, November 2025. https://www.anthropic.com/engineering/advanced-tool-use
Jones, Adam and Kelly, Conor. “Code Execution with MCP.” Anthropic Engineering Blog, November 2025. https://www.anthropic.com/engineering/code-execution-with-mcp
Wolenitz, Alon. “Advanced Tool Use in Claude API: Three New Features That Change A Lot.” Setec Research Claude Blog, November 2025. https://claude-blog.setec.rs/blog/advanced-tool-use-claude-api
Cloudflare Engineering. “Code Mode: Give Agents an Entire API in 1,000 Tokens.” Cloudflare Blog, September 2025. https://blog.cloudflare.com/code-mode-mcp/
Anthropic. “Introducing the Model Context Protocol.” Anthropic News, November 2024. https://www.anthropic.com/news/model-context-protocol
Anthropic. “Donating the Model Context Protocol and Establishing the Agentic AI Foundation.” Anthropic News, December 2025. https://www.anthropic.com/news/donating-the-model-context-protocol-and-establishing-of-the-agentic-ai-foundation
Linux Foundation. “Linux Foundation Announces the Formation of the Agentic AI Foundation (AAIF).” Linux Foundation Press Release, December 2025. https://www.linuxfoundation.org/press/linux-foundation-announces-the-formation-of-the-agentic-ai-foundation
Anthropic. “Introducing Claude Sonnet 4.6.” Anthropic News, February 2026. https://www.anthropic.com/news/claude-sonnet-4-6
Pobar, Joel. “LLMVM: LLM Python Agentic Runtime Prototype.” GitHub Repository. https://github.com/9600dev/llmvm
Model Context Protocol Specification, Version 2025-11-25. https://modelcontextprotocol.io/specification/2025-11-25
Pento AI. “A Year of MCP: From Internal Experiment to Industry Standard.” Pento Blog, 2025. https://www.pento.ai/blog/a-year-of-mcp-2025-review
Claude API Documentation. “Tool Search Tool.” Anthropic Developer Platform. https://platform.claude.com/docs/en/agents-and-tools/tool-use/tool-search-tool
Claude API Documentation. “Programmatic Tool Calling.” Anthropic Developer Platform. https://platform.claude.com/docs/en/agents-and-tools/tool-use/programmatic-tool-calling

Tim Green UK-based Systems Theorist & Independent Technology Writer
Tim explores the intersections of artificial intelligence, decentralised cognition, and posthuman ethics. His work, published at smarterarticles.co.uk, challenges dominant narratives of technological progress while proposing interdisciplinary frameworks for collective intelligence and digital stewardship.
His writing has been featured on Ground News and shared by independent researchers across both academic and technological communities.
ORCID: 0009-0002-0156-9795 Email: tim@smarterarticles.co.uk
Software cannot be estimated the way your organization wants, and it's time to stop trying
from  Reflections
Reflections
Managers and organizations want to know exactly when features, bug fixes, and other work will be done. Many have not been software engineers themselves, so they ask for exact dates. Sure, you can be off by a day or two—maybe!—but more than that, and it's a problem. After all, their boss needs to know what to promise customers. What's so hard about knowing when you'll be done?
Sadly, software cannot be estimated that way, and we need to stop pretending otherwise. It's a myth—a pervasive one—and perpetuating that myth only perpetuates its harm.

Sure, if a task is almost identical to some previous task, a precise and reliable estimate really can be communicated. Unfortunately, that almost never happens. If the work ahead were so similar, someone would have done it already using copy and paste. If it's similar and the engineering team wanted to set themselves up for success later, they'd refactor the system, but that refactoring itself can be a hazy fog of unknowns. We've all been there many times.
The problem
I once worked with someone who liked to compare software development to parcel delivery: choose a day when the package is expected to arrive. It's okay if there needs to be a delay, as long as that delay is communicated clearly. While the flexibility with delays was genuinely appreciated, the broader analogy soured on me over time. In truth, estimating software is nothing like estimating package delivery. The former involves doing something that has never been done before, while the latter is completed billions of times each year. Does Amazon have an advantage when forming estimates? You'd better believe it.
Software development is one of the only professions where we are asked to accurately state how long it will take us to do something that has never been done before in the history of the universe.
—Unknown, from a screenshot on X
How long will it take for Amazon to deliver a board game to Zara in Cincinnati? Well, probably about as long as it took last time. Yes, every delivery is different, but there must be millions of deliveries of similar items to nearby locations with similar weather forecasts and other pertinent factors being similar or identical. How long will it take? Probably that long.
By contrast, how much time will be required for me to change code I've never seen? I truly have no idea. How about adding, say, karaoke support to a streaming music app, one with millions of lines of code I've never read, where myriad caveats exist for different software clients, different spoken languages, and different copyright laws. How long will that take? Except in extremely broad terms, your guess is as good as mine. It will take more than one week, and it can probably be completed in less than one year. Beyond that, there's not much more that can be promised, at least in the beginning. More on that in the next section.
No, estimating software development is nothing like estimating like parcel delivery. It's more like estimating the pace of scientific progress. We simply don't know what we don't know. We can't know until we do it.
As much as possible, organizations should communicate that software will be ready when it’s ready. If some software must be released by a certain date, the feature list should not be guaranteed. I know this is easier said than done, believe me, but reality is what it is. Software simply cannot be estimated the way organizations imagine. Some higher-ups, especially those who have not been software engineers, may find this outrageous. They may demand exact estimates regardless. To them, I would say, “Fine, but let’s be honest, how’s that working for ya? How often are you given estimates that actually turn out to be correct?”

There's a reason you're reading this blog post. Something isn't working, and it's not about discipline. It's not about communication. It's not about skill. You're on the wrong path. Skeletons and vultures surround you. It's time to turn around.
Thankfully, there is a better way. Your manager may not like it at first, but over time, they may come to see that estimates of this type are actually useful, unlike the estimates they are accustomed to.
The solution
To explain this kind of estimation, I need to define two terms. First, I'm using the term accurate to describe any estimate that is correct within a given range of dates. Defined this way, even a very broad estimate can be accurate. For example, an estimate that a feature will be completed some time between March 1st and December 31st would be accurate, as long as it turns out to be true. Precision is another matter. That feature estimate isn't very precise, but it would be more precise if it predicted a completion date between, say, April 1st and July 1st. This is how Rapid Development defines the terms, and I think it’s a good approach. In fact, most of this advice is lifted from Rapid Development. I recommend reading it. It's a tome, so focus on the sections that are most pertinent to your needs.
Crucially, estimates can and should become more precise as time goes on and details become more clear. If a team begins with an estimate of some time in Q1 or Q2, but the feature is more difficult than expected and they realize they need to revisit the database schema, perhaps the estimate could be narrowed to some time between May 1st and June 15th. If the team is nearing the end and the final code reviews go more smoothly than expected, maybe the estimate could narrow to some time between May 16th and May 31st. If a critical issue is found elsewhere in the codebase, taking the team off the feature for a while, maybe May 29th becomes the most likely date of completion. The point is, there's no way to predict those problems in advance, but they can inform better estimates over time, as long as the estimation method supports that. Did you instead randomly pick a day three months in advance? Too bad. You're screwed.
Reality-driven estimation
So how should we estimate? Strive for accuracy, start with low precision, and seek greater precision over time. As another example, you might consider communicating a project end date some time between Q2 and Q4, then later refine that to some time in the fall, then some time in October. Finally, at the very end of the project, you might be able to promise a specific week or even a specific day. That is an approach to estimation which acknowledges reality. That is an approach to estimation which acknowledges that surprises happen.
Do organizations want to hear this? Unfortunately, no, I don't think so. It's a tough sell. Organizations want certainty, and they want it now. Good luck telling your boss that you don’t know exactly how much time and money you're going to spend. Even the project management apps we use typically require that an estimate be recorded as a specific date. Talk about encouraging bad practices.
Pushing back is hard, and as someone who was raised to never question authority, even when that authority is obviously wrong, I happen to be particularly bad at it. That's too bad. Our bosses pay the bills, but we do the work. It's time we start saying, “The work can't be done that way, and if I were to tell you otherwise, I'd be lying to you.”
Reality is what it is, and the best we can do is provide estimates with gradually improving precision. Organizations can pretend otherwise, and countless surely will, but again, I would ask, “how's that going?” Organizations ignore these facts to their own detriment, at the cost of time, money, and frustration. I wish them luck.
For everyone else, consider embracing reality. It's not perfect, but it's the best we can do.
#Life #Quotes #SoftwareDevelopment #Tech
from  Kroeber
Kroeber
#002307 – 22 de Setembro de 2025
O argumento dos doomers, sobre o perigo de uma superinteligência artificial que, por um ou outro motivo leva à nossa extinção, não é simplesmente uma visão pessimista sobre um tipo específico de tecnologia. Muitos destes hiperpessimistas vêm do movimento e filosofia altruísmo eficaz, que é quase uma consequência inevitável de se levar (como Peter Singer) a lógica do utilitarismo até às últimas consequências. Para os proponentes do EA (a sigla geralmente usada para referir o effective altruism), deve-se maximizar o bem que se faz pelos outros e, por isso, a única opção ética é concentrarmo-nos nas acções e causas que beneficiem mais pessoas durante mais tempo. É daqui que emerge a obsessão com o apocalipse trazido por uma inteligência artificial. Sendo o dano máximo (a extinção da espécie humana), prevenir este resultado nefasto é logicamente mais importante que qualquer outra causa. Mesmo sendo a probabilidade de acontecer relativamente pequena, prevenir que suceda traz o máximo de bem (salvar a vida) ao máximo de pessoas possível (a humanidade inteira).
O que é curioso é que os boomers (que defendem a expansão da tecnologia com a máxima rapidez e urgência) usam a mesma lógica. Mesmo não havendo certeza de que seja possível produzir uma super inteligência artificial, os benefícios (curar o cancro e outras doenças, resolver as alterações climáticas, acabar com as guerras e com a fome) são imensos, basicamente resolver todos os problemas humanos. Por isso, segundo os princípios ultra-utilitários do EA, nenhuma outra causa é tão importante como fazer emergir essa mega-entidade digital. Porquê gastar recursos a melhorar os problemas ambientais, ou aliviar a fome, ou investir esforços diplomáticos para acabar com conflitos, se uma superinteligência artificial resolveria todos esses problemas.
O que um e outro campo parecem professar não é, como dizem, o uso da razão, mas uma nova forma de religião. E estão em desacordo simplesmente no método: uns querem impedir que o diabo venha ao mundo e os outros querem invocar a vinda de deus. Usam argumentos lógicos para defender que deixemos de cuidar uns dos outros, das nossas sociedades e do planeta, porque partem de um pressuposto que paira sobre mas não se baseia no estado actual da ciência informática. Ora aqui vai um outro argumento: mesmo que fosse verdade que vem aí um deus ou um diabo digital, devemos cuidar uns dos outros, apenas porque isso determina como construímos as sociedades, as relações humanas e a própria tecnologia. Não devemos colocar nas mãos da tecnologia nenhuma decisão de vida ou morte (como agora se faz com as armas autónomas). O altruísmo poderá ter mesmo uma base bio-evolutiva, os comportamentos pró-sociais beneficiam também quem os praticas e são mais do que a soma de todos os benefícios gerados. São a própria coesão das nossas sociedades, das nossas famílias, da humanidade. Devemos resistir à tentação de industrializar até o altruísmo.
09/03
from Manuela
“Se estamos destinados a ser, eu te vejo mais tarde.”